Introduction
In many organizations, third-party onboarding begins with identifying and evaluating individual vendors, suppliers, or partners based on specific business needs or requests. SAFE’s manual onboarding flow is designed to support this scenario by allowing you to search for and add a single third party at a time.
This method is ideal when:
You need to quickly evaluate a specific vendor not yet in your system.
You want to directly configure automation and assessment settings for each third party.
Using SAFE Agents, the manual onboarding flow makes it easy to find a third party by name and automatically retrieve their public firmographic data, such as industry, revenue, and domain information. You can then enrich this record by selecting applicable business resources and choosing how much of the onboarding and risk assessment process you want to automate.
Whether your organization follows a manual, semi-automated, or fully automated onboarding process, this workflow provides flexibility to tailor the experience for each individual third party.
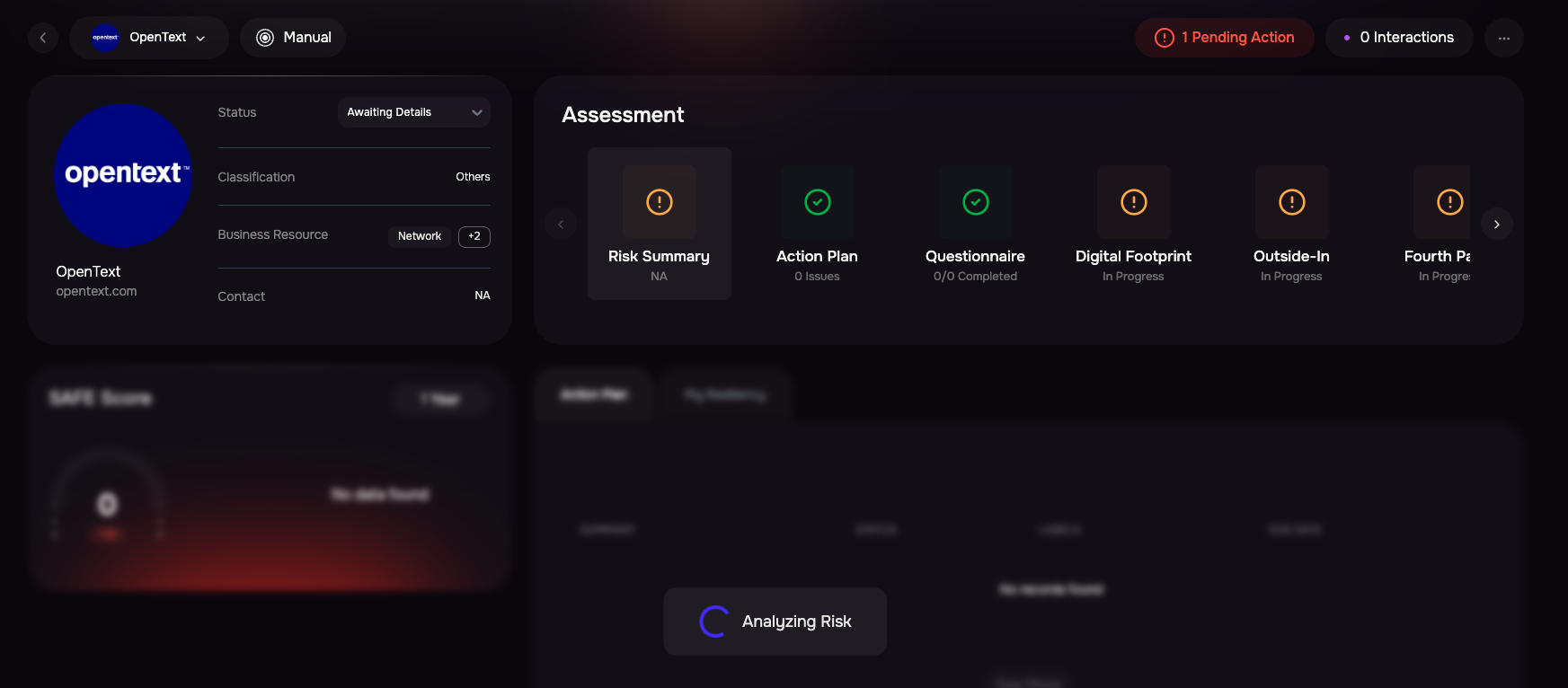
Once onboarded, SAFE’s AI agents will begin evaluating the third party’s risk posture using publicly available data, domain scans, and threat intelligence—saving you time and accelerating your due diligence process.
Manually Add a Third-party
Navigate to the Third-Party option from the left-navigation.
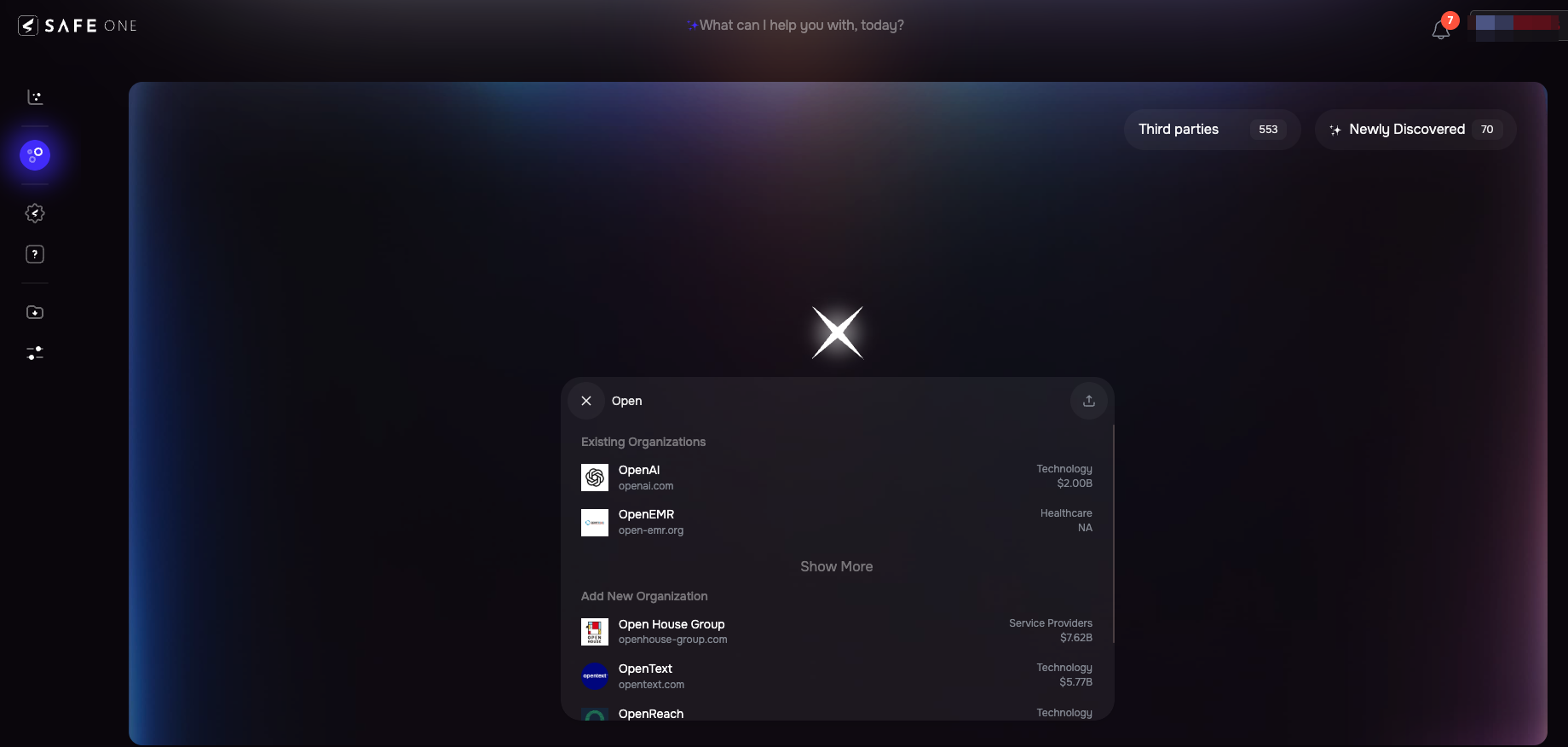
In the search bar, begin typing the name of the third-party organization.
The search page returns the result in two sections:
Existing organization: These are organizations that have already been added to SAFE. Clicking on one will take you directly to that organization's page.
Add new Organization: These are new organizations discovered by SAFE’s Agent. Click the most suitable result here to begin onboarding a new third party.
Select the third party from the search suggestions.
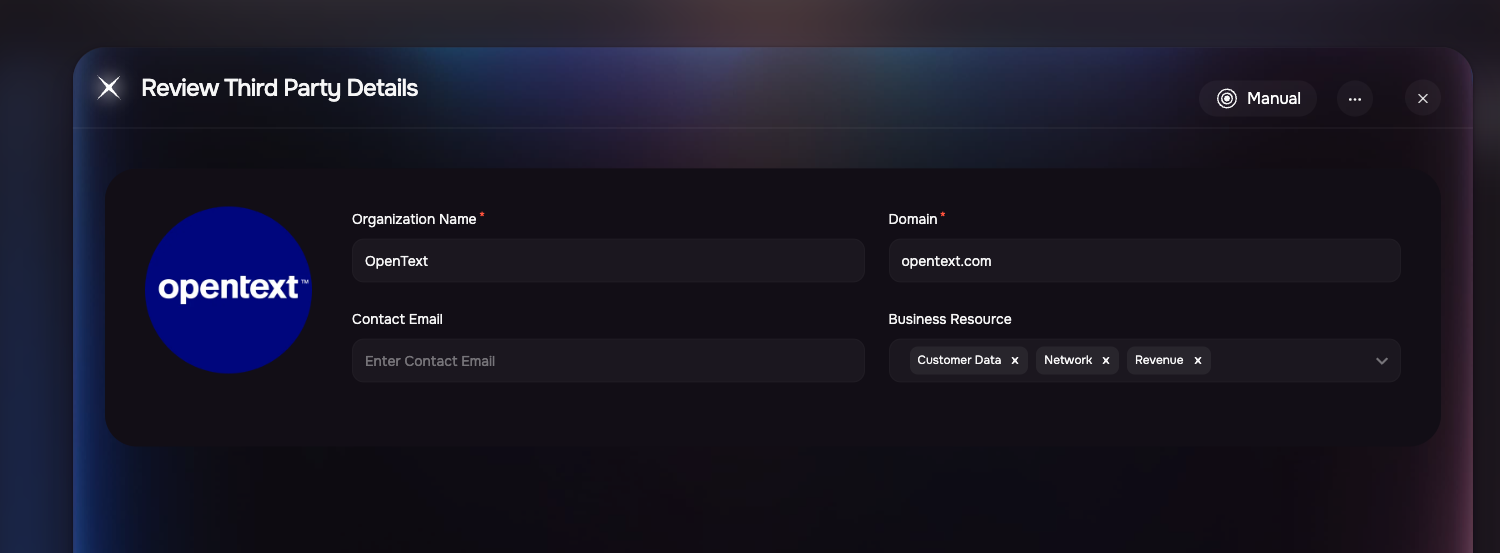
SAFE automatically fetch and display key firmographic details such as:
Company Name
Industry
Revenue
Domain
Other metadata
Review and confirm the auto-populated firmographics (e.g., Business Name, Fully Qualified Domain Name).
Select Business Resources relevant to this relationship (e.g., Customer Data, Network Access, Revenue Dependency).
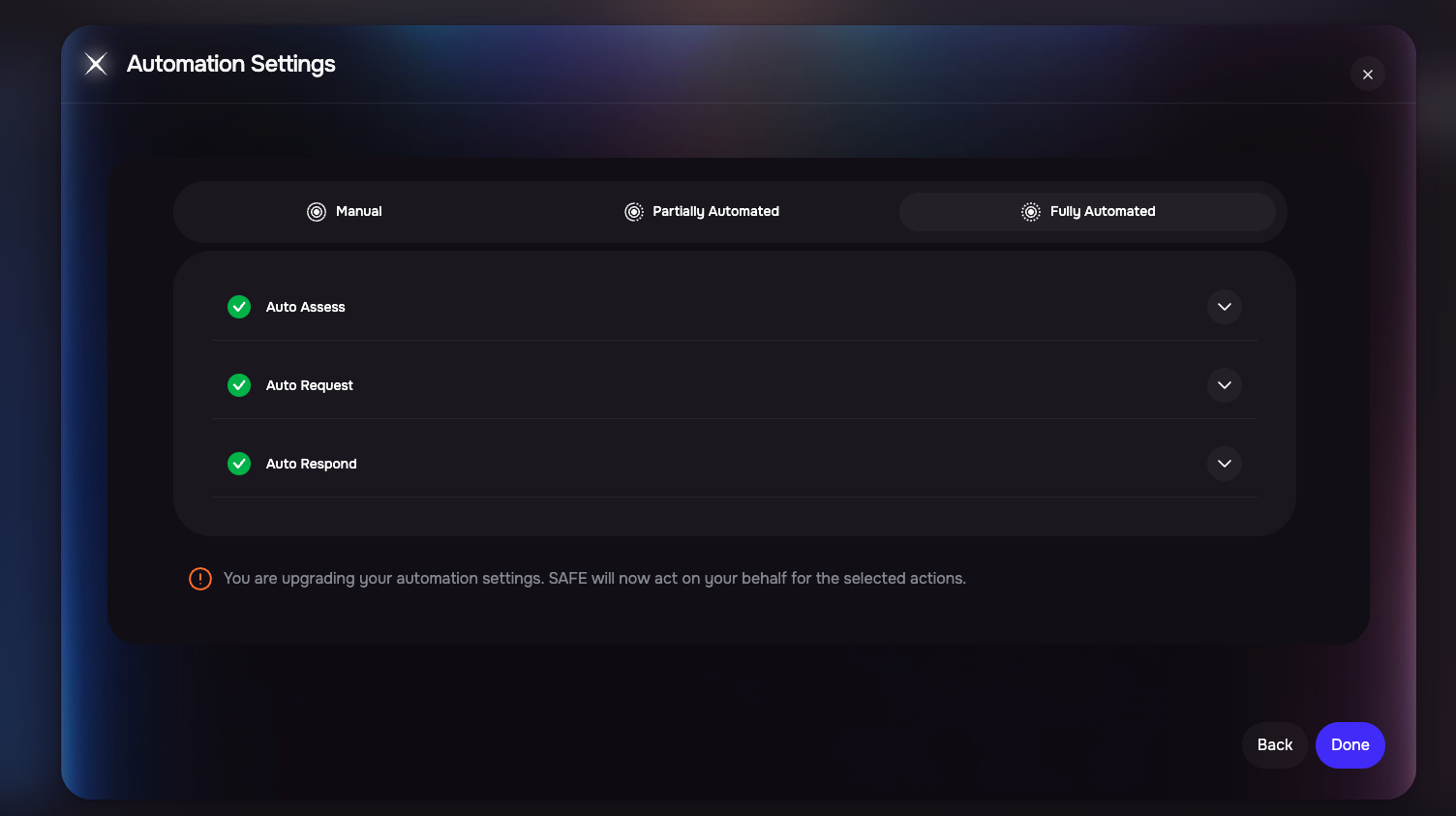
Select an Automation Mode:
Manual – Fully manual process; contact email is optional.
Partially Automated – Pre-fills based on outside-in assessment; contact email is optional.
Fully Automated – AI handles questionnaire outreach and auto-filling; contact email is required.
If using Fully Automated mode, enter the contact email for the third party.
Click the Add Organization button to initiate the onboarding process.
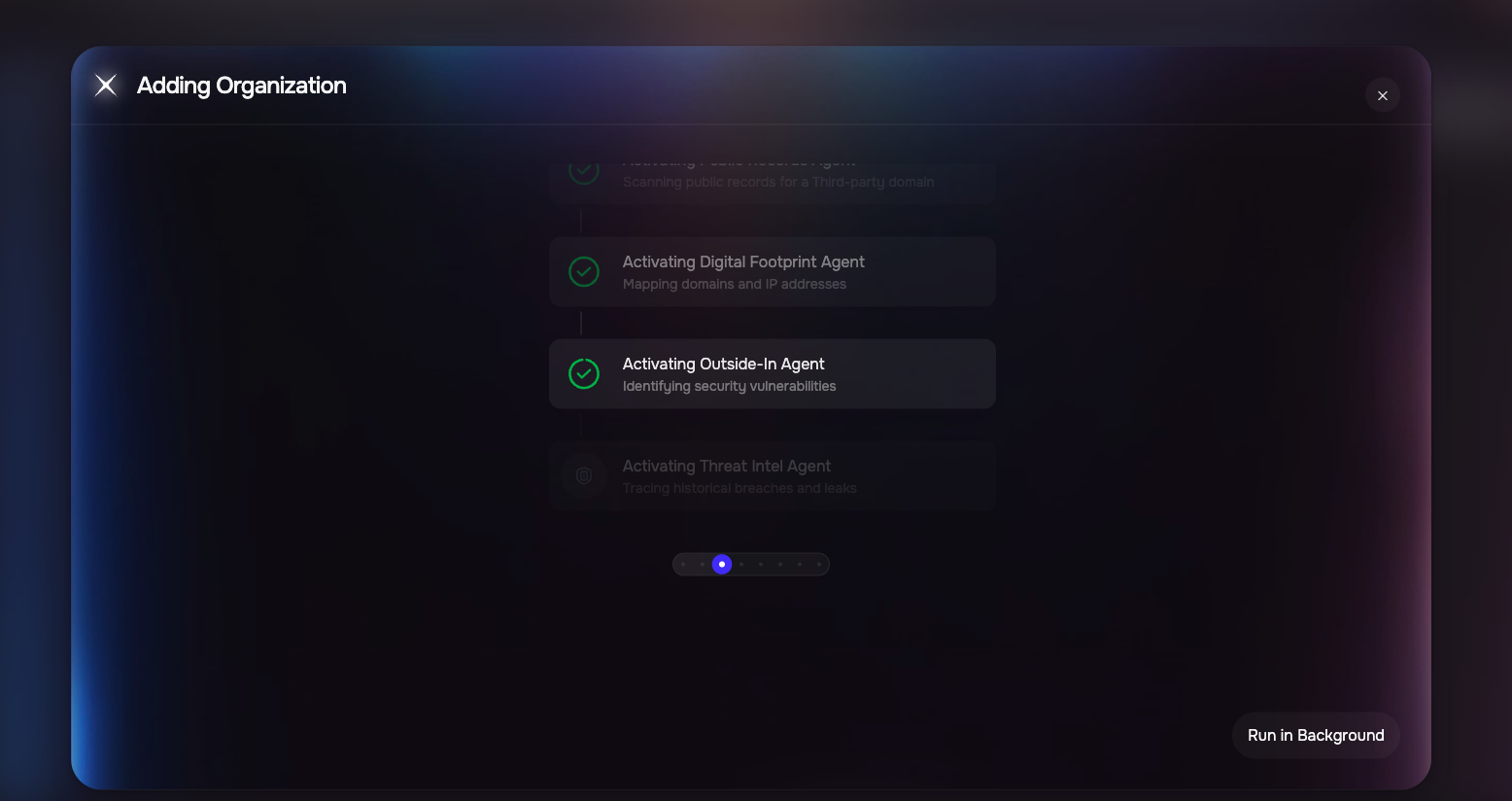
The system triggers the multipel SAFE’s AI agents one-by one to evaluate the third party’s risk posture using publicly available data, domain scans, and threat intelligence.
Public Records Agent checks SEC filings, privacy/security policies.
Threat Intelligence Agent scans for known breaches or threats.
Outside-In Assessment Agent runs a scan on the domain to discover vulnerabilities or misconfigurations.
The AI agents answers the associated questionnaier partially or fully based on this data.
The system completes the initial risk assessment completes witin 3–5 minutes.