New Features and Enhancements (SAFE Version 3.0.46)
Release Date: 22nd Feb 2023
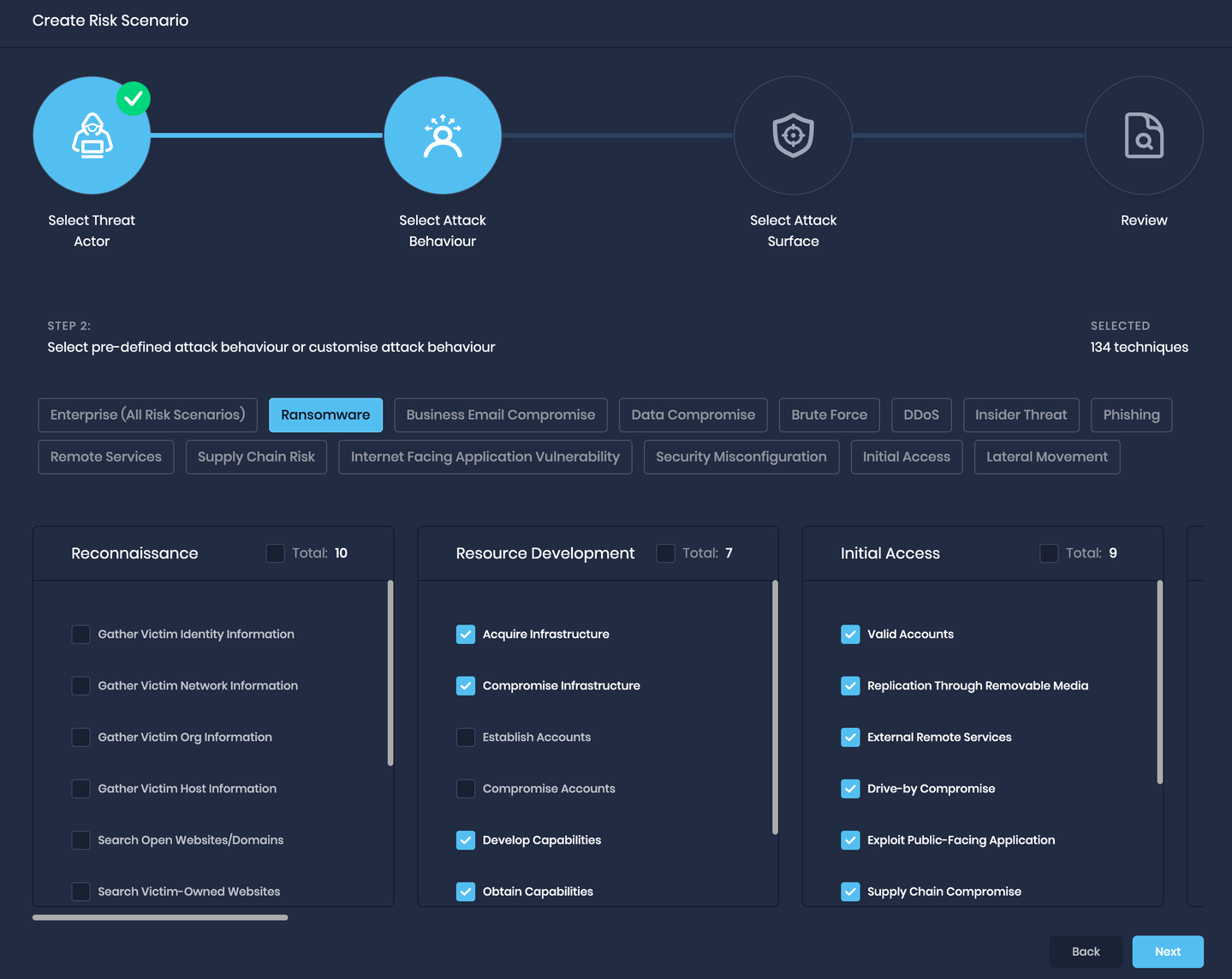
1. Custom risk scenario creation is made easy with pre-defined attack behavior in SAFE
SAFE's Bring Your Own Risk (BYOR) feature now offers quick filters that simplify the process of creating custom risks by pre-defining attack behavior. These filters are accessible on the Risk Creation page and automatically select the corresponding attack behaviors when applied.
2. Enhancements in Risk Scenarios
- The Risk Scenario table has been expanded to include three new columns that show the timestamps for when the risk was last assessed, updated, and by whom.
- SAFE now also displays the number of risk scenarios for each tab on the Risk Scenario page.
- The Financial Risk widget has been removed from the individual risk scenario page where it is not relevant.
- By default, the Enterprise Risk Scenario is marked with a star, and all risk scenarios are labeled next to it.
- SAFE is now configured to only display qualified and failed techniques by default in the ATT&CK matrix view.
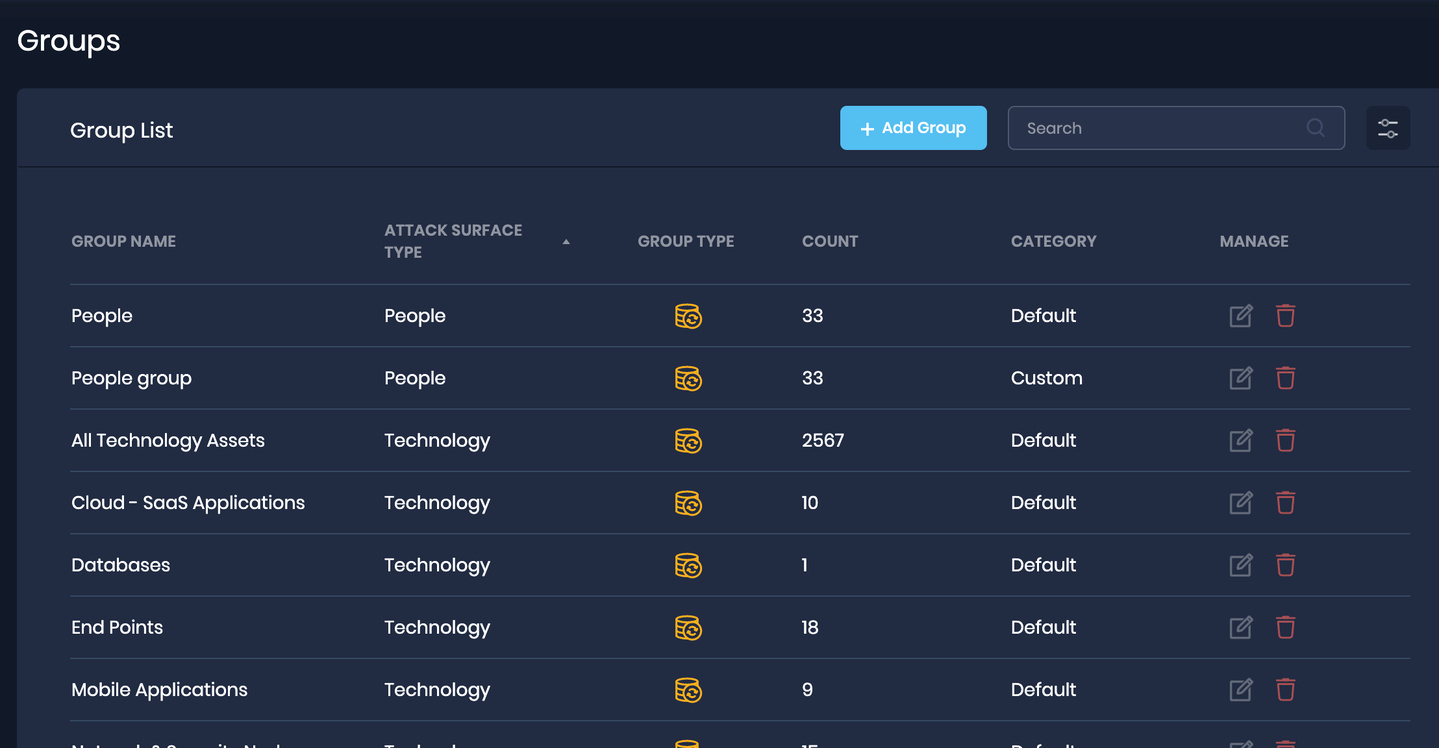
3. Enhancements in Groups
We have added a new column, "Attack Surface Type," in the Group list on the Groups page to quickly identify the Technology and People Group.
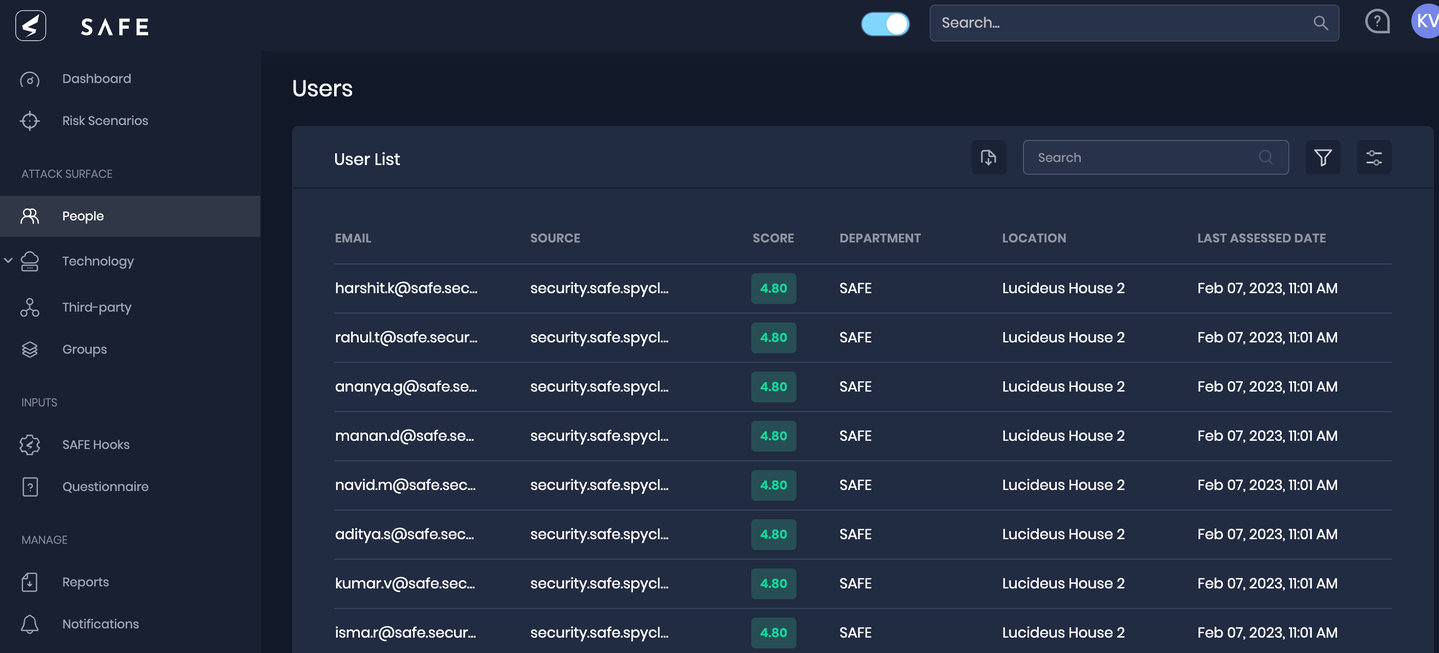
4. Enhancements in People
- Clicking People in the left navigation directly redirects you to the User's page.
- The People vertical has been removed from the Technology vertical list on the main SAFE dashboard.
- We have enhanced the User's list table to remove the checkboxes, Technology Vertical filter, and Assess button.
New Features and Enhancements (SAFE Version 3.0.45)
Release Date: 07th Feb 2023
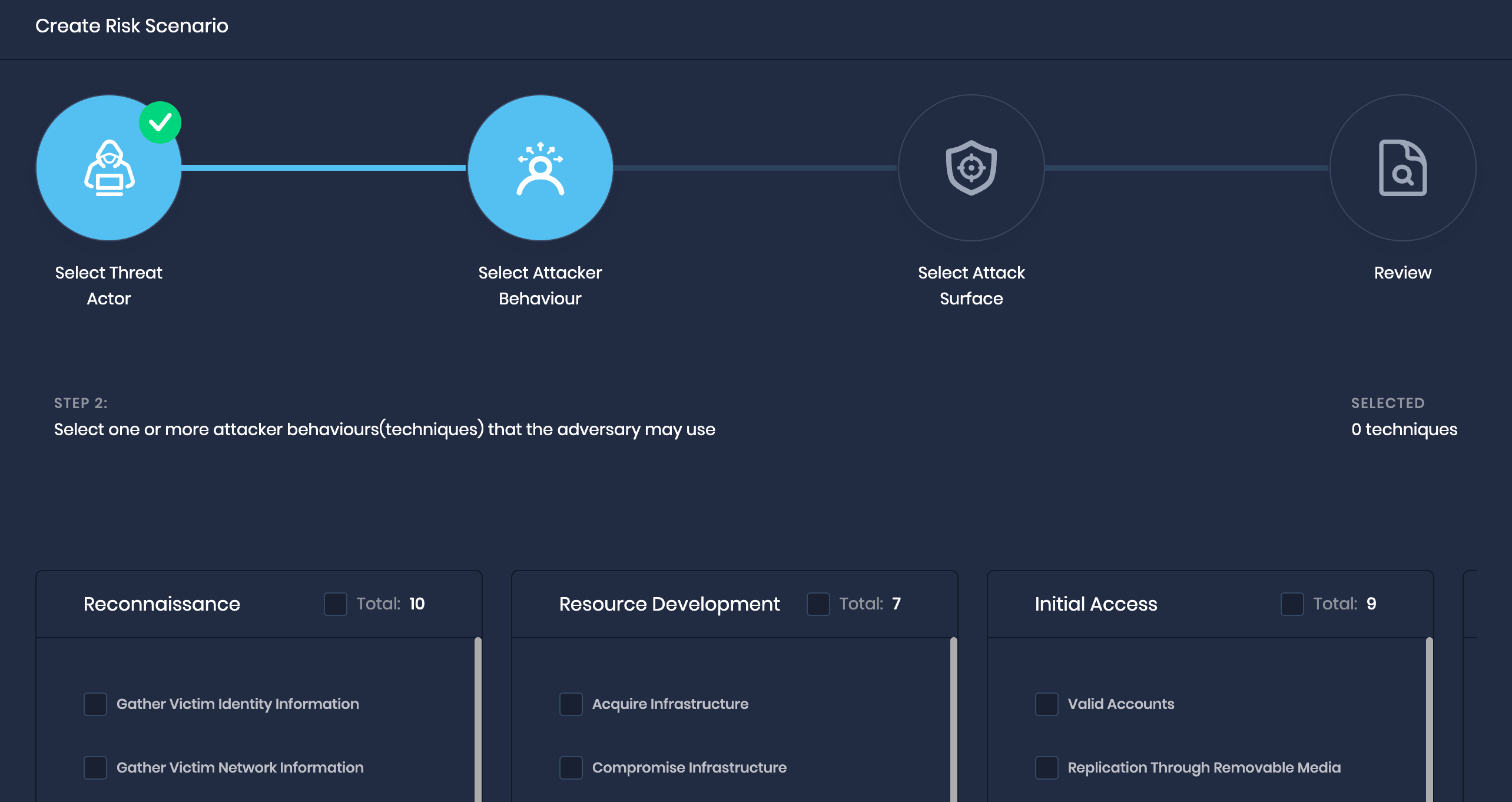
1. Introducing Bring Your Own Risk (BYOR)
The Bring Your Own Risk (BYOR) feature in SAFE allows users to create and manage custom risk scenarios, providing a more specific view of the security posture of their organization and the ability to improve it.
A new button, "Create Risk Scenario," has been added to the Risk Scenario page, which allows users to configure custom scenarios based on Threat Actor, Attacker Behavior, and Attack Surface.
SAFE provides breach likelihood and actionable insights for each custom scenario, with a maximum of 10 custom scenarios. Additional scenarios can be added by contacting the SAFE Support team.
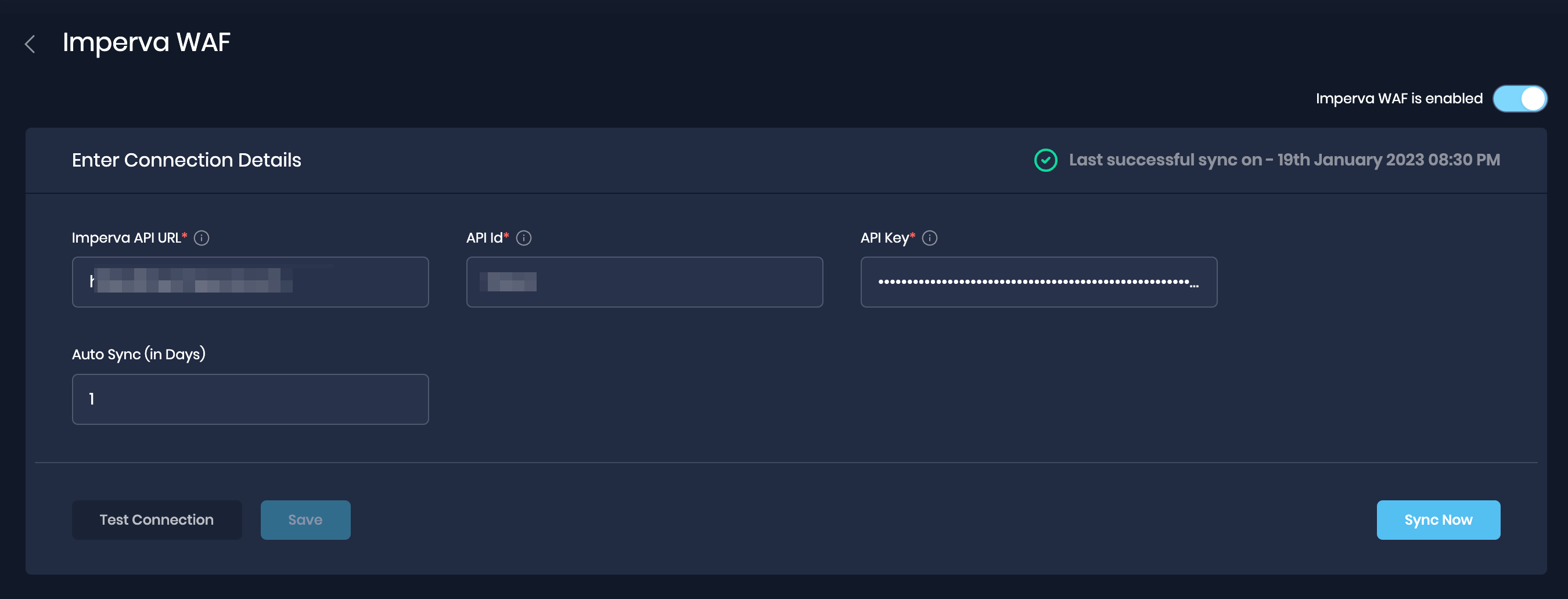
2. Integration with industry-leading Web Application Firewall (WAF) - Imperva WAF
The integration of SAFE with Imperva WAF allows for the assessment of web applications protected by Imperva's WAF service. It checks for misconfigurations in the WAF rules and includes them in the overall risk posture of the organization. The integration also includes WAF controls in different risk scenarios, such as DDoS, which can prevent certain types of cyber attacks.
SAFE administrators can set up the integration by using the Imperva card on the SAFE Hooks page.
3. Uploading phishing results made easier
We have made it easier for you to upload the Phishing results by adding a Phishing Report Upload functionality. Users can now upload results obtained from any phishing tool by downloading the report, converting it to a format supported by SAFE, and uploading it to the new Phishing Report Upload card on the SAFE Hooks page.
Additionally, the page displays a history of all report uploads.
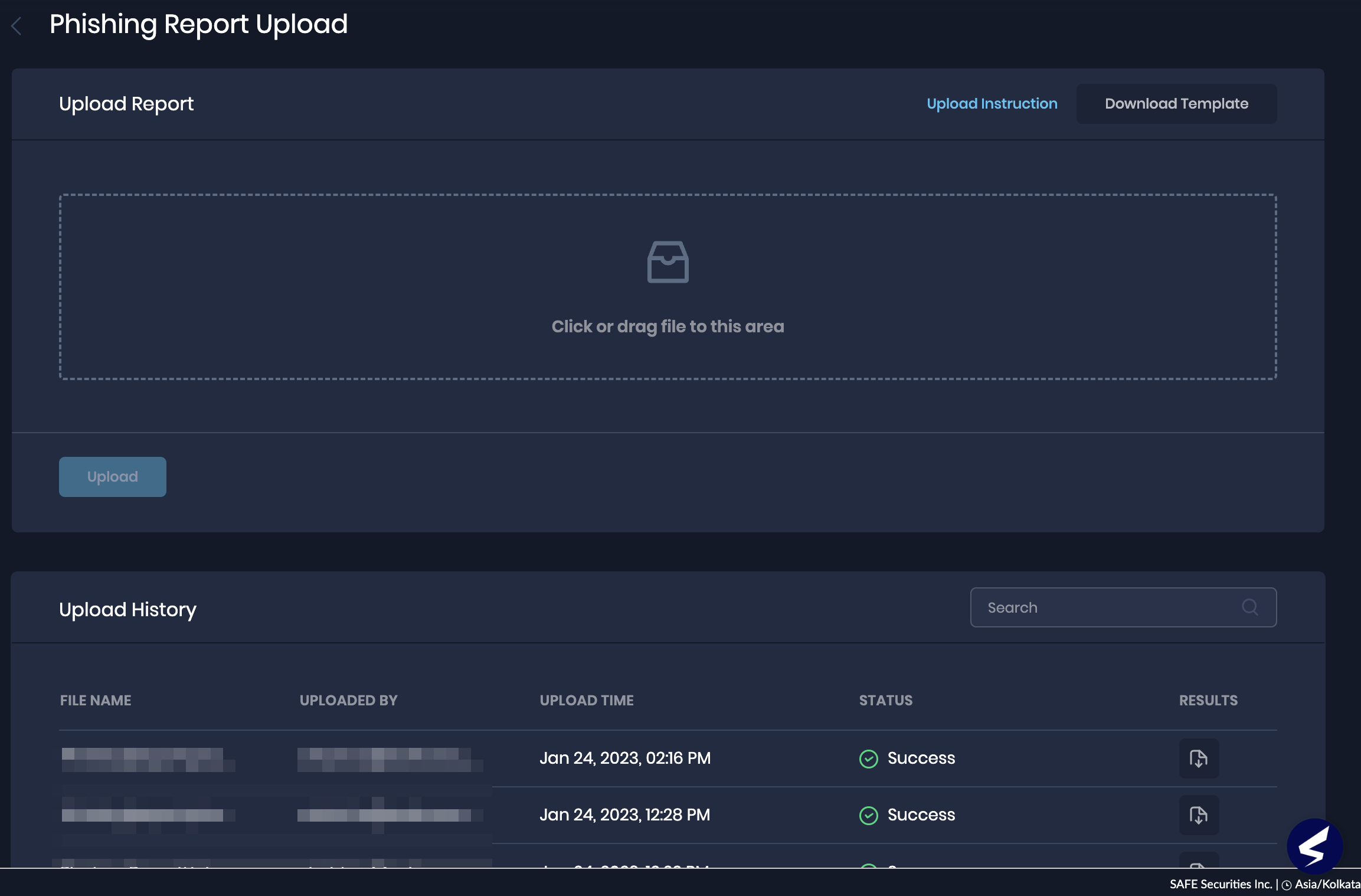
- CSV files in the template format of up to 10 MB are allowed.
- The CSV file supports upload for up to 50K rows.
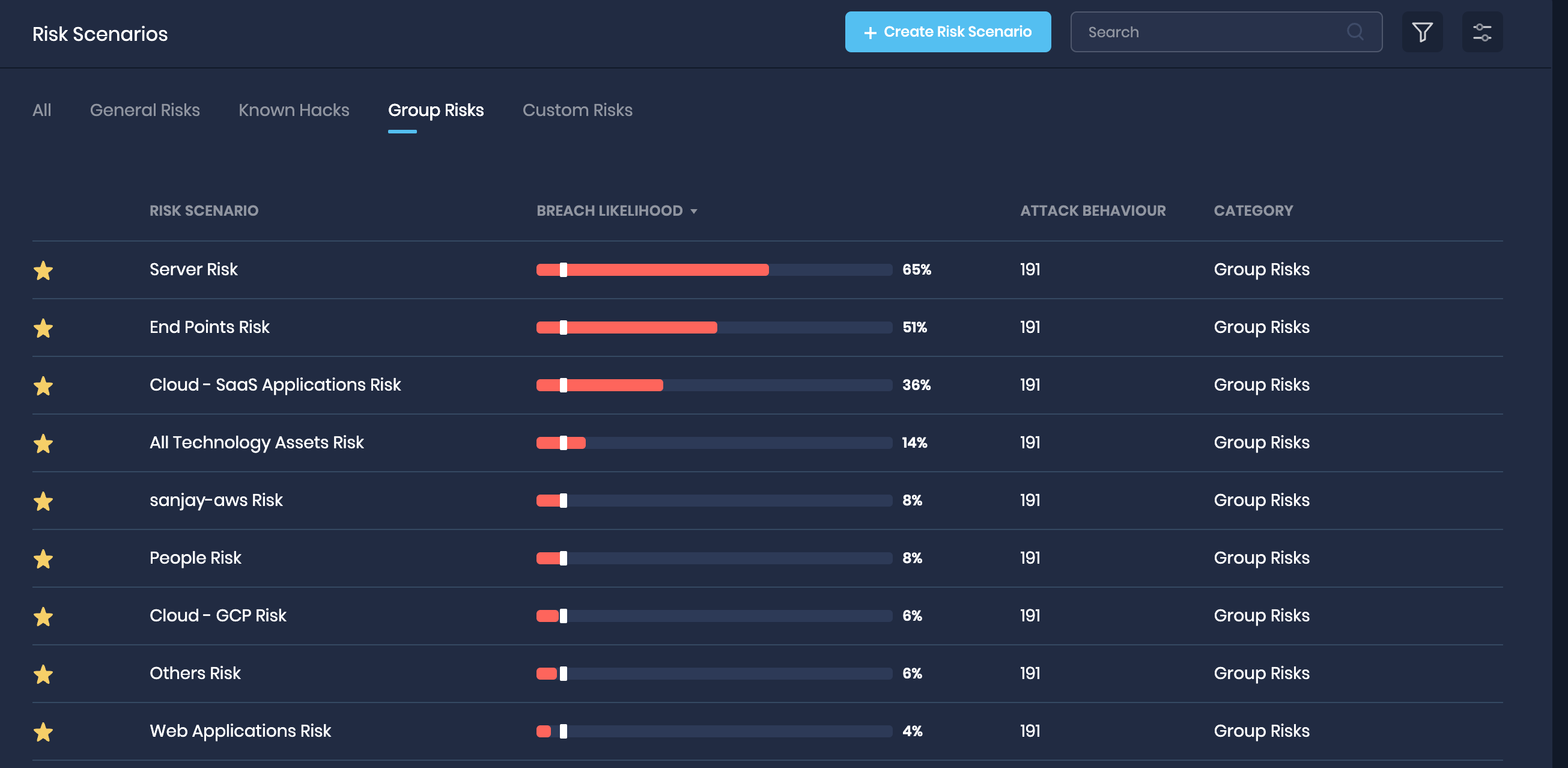
4. Risk Scenarios for Technology Assets
For better insights into the technology risks, we have added OOTB (out-of-the-box) Risk Scenarios for each of the technology verticals, such as Cloud SaaS Applications, Cloud Azure, Servers, Middleware, etc., in SAFE.
Now users can directly go to the Risk scenario page, find the technology asset group risk scenario, and view the details such as Breach Likelihood, Prioritize Actionable Insights, and MITRE ATT&CK Mapping. You can also view the attack surface (assets) belonging to the risk scenario.
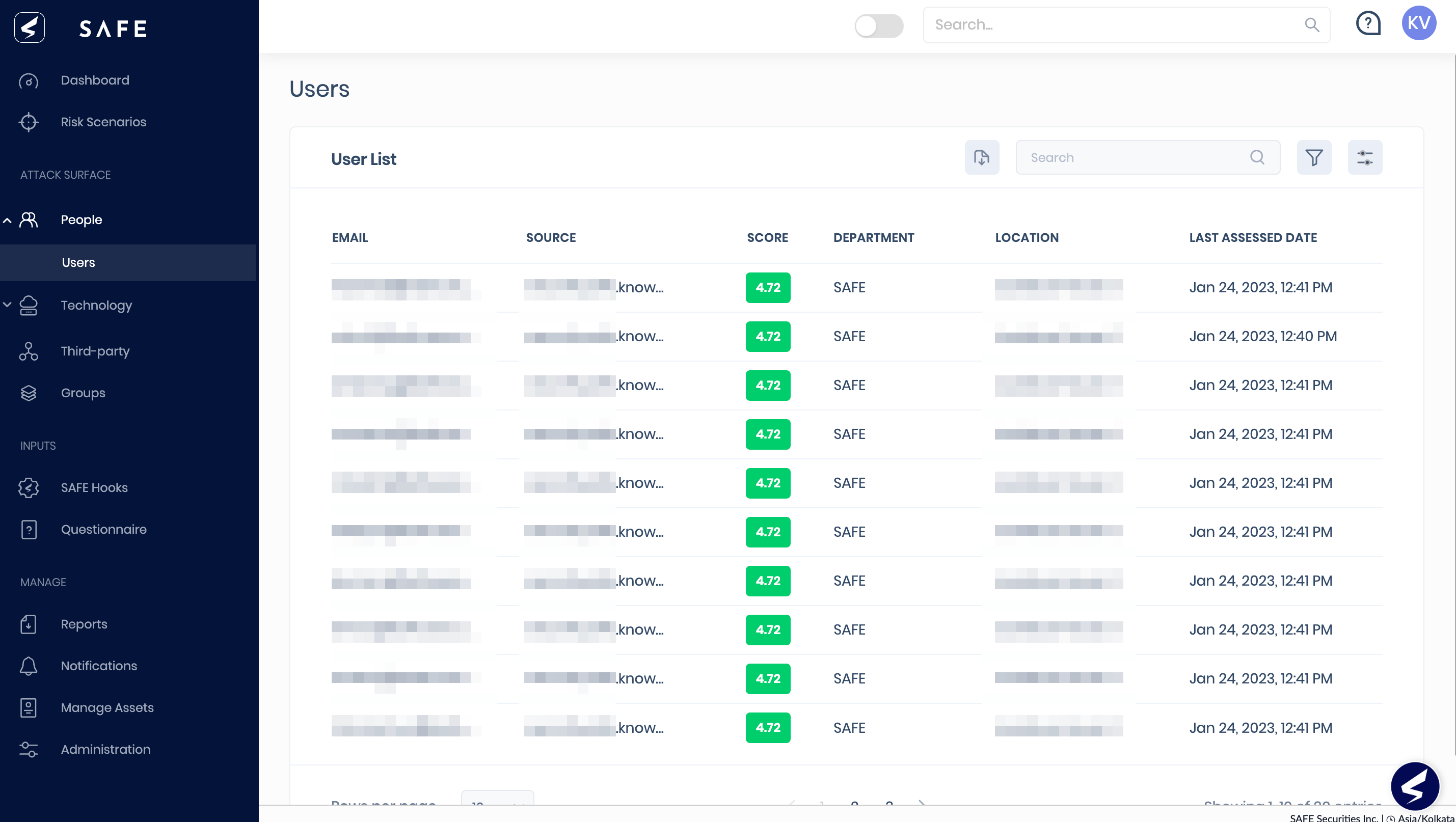
5. Introducing People as Attack Surface
We have completely revamped the People assessment, and now SAFE treats People as an attack surface (just like a technology asset) in SAFE.
Now the new People page contains a list of all users with the details such as user source, Email, Location, SAFE Score, and last assessed date.
The system redirects you to the user's details page by clicking a user from the list. Here you can find the controls and their status. Further, by clicking on a control, you can view the MITRE ATT&CK TTPs mapping for the control.
6. Introducing Groups in the left navigation
To keep the asset grouping consistent across all the attack surfaces within SAFE, we have added the Groups option in the left navigation.
The Group lists all the asset groups and user groups in SAFE. From this option, users can create and manage asset groups or user groups in SAFE.
Also, we have added Asset Group Category (Default and Custom) in the group list table.
7. Enhancements in Cyber Security Products (CSP) and Policy assessment in SAFE
7.1. Cyber Security Products Assessment
We have made the Cyber Security Products (CSP) assessment user flow easy by adding the assessment options; Not Assessed, Qualified, Failed, and Not Applicable on the Cyber Security Products page.
- NotApplicable: Select this option if the Cyber Security Product does not apply to your organization.
- NotAssessed: Select this option if the Cyber Security Product applies to your organization, but the assessment still needs to be completed.
- Qualified: Select this option if the Cyber Security Product passes the assessment. It is important to define the coverage status percentage by sliding the coverage status sliding bar toward the right to the appropriate percentage.
- Failed: Select this option if the Cyber Security Product fails the assessment.
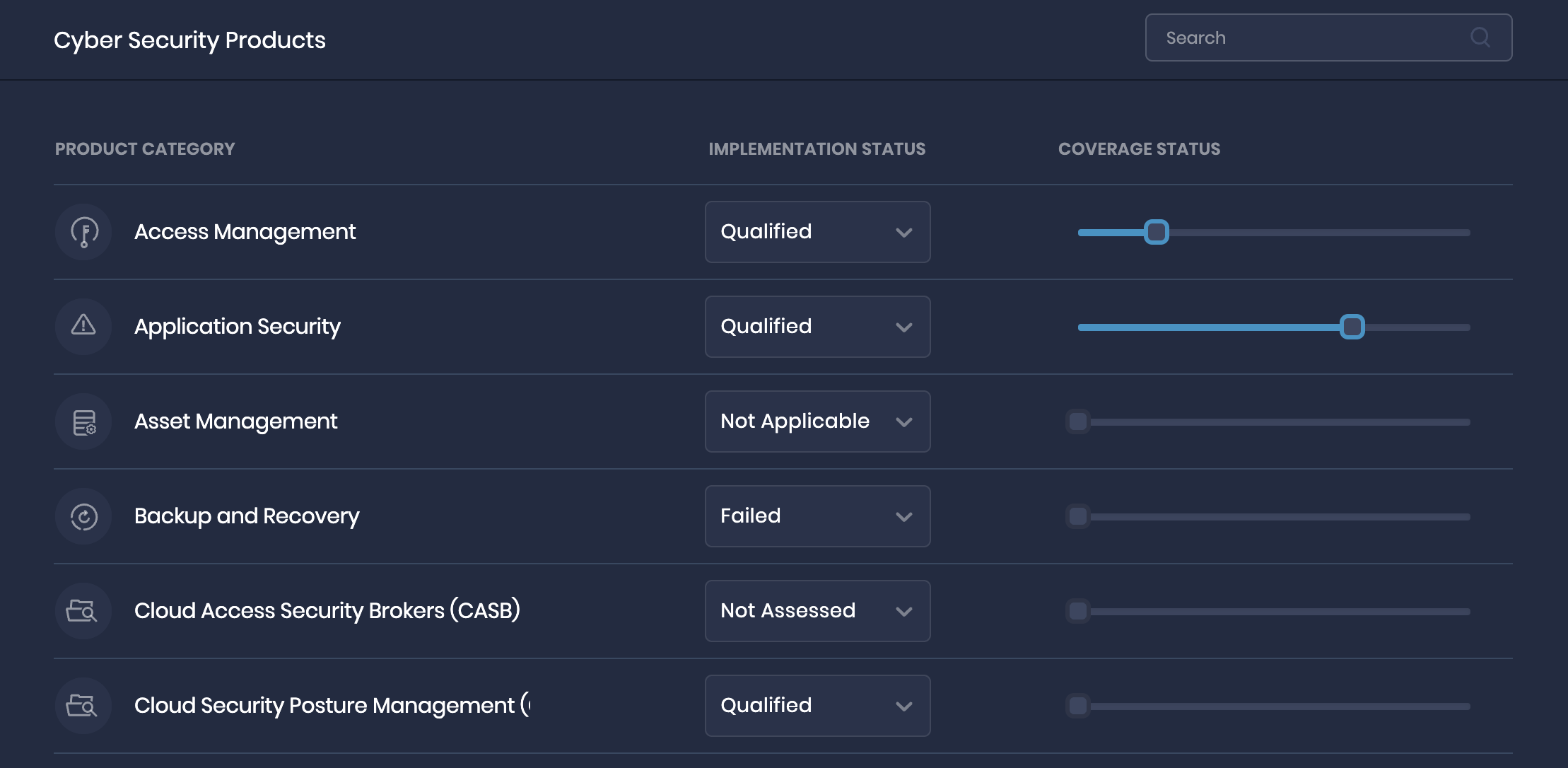
- By default, Cyber Security Products implementation status is Not Assessed, and it impacts the SAFE Score.
- With the ability to mark a Cyber Security Product as Not applicable to your organization on the Cyber Security Products page itself, we have removed the Cyber Security Products Management page from the administration.
7.2. Policy Assessment
We have recalibrated the list of policy controls with the Cyber Security Products and, as a result, removed a few redundant controls and updated existing controls from the Policy Assessment in SAFE.