Introduction
Single Sign-On (SSO) enables organizations to use the SAML 2.0 authentication provider for authenticating login into SAFE. Admin can onboard and manage users right from their Okta SSO platforms, eliminating the need to maintain a separate user authentication mechanism for SAFE.
Info
SAFE does not support IdP-initiated SSO flow.
To navigate directly to SAFE and log in from within your Okta enterprise application, you must request that Safe provide a URL that can be bookmarked in Okta.
Setting up Okta
- Click on Applications from the left navigation bar in the Okta developer console.
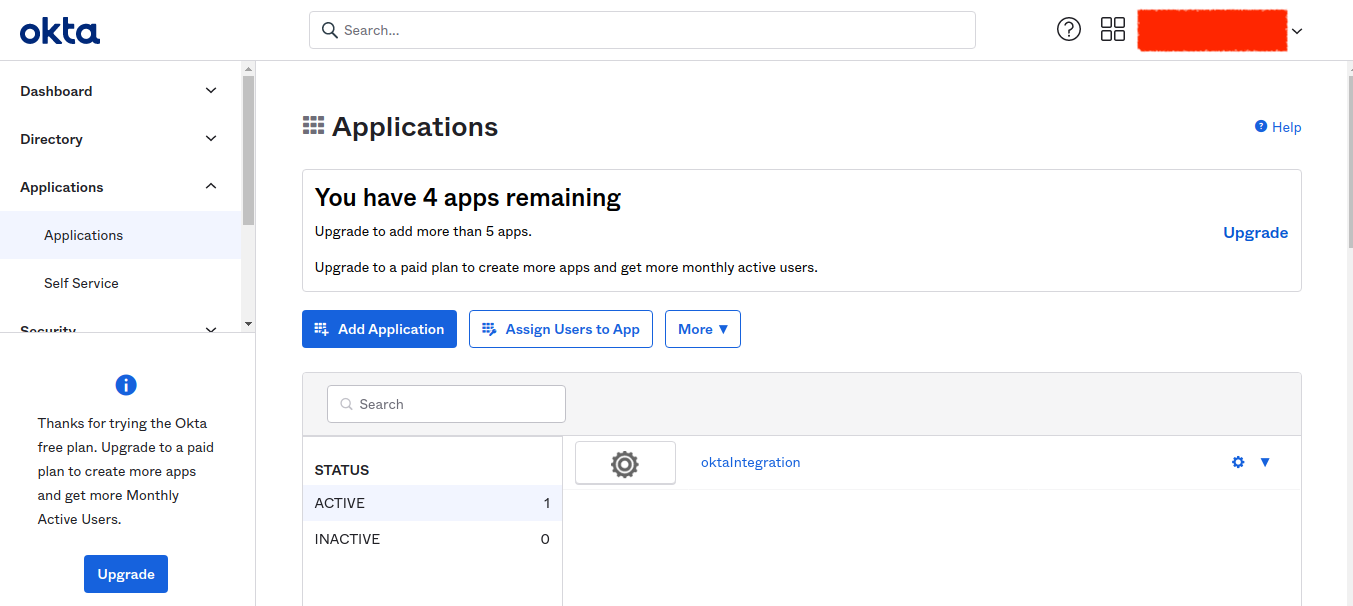
- On the Add Application page, click the Create New App option.
- For the Sign-on method, choose SAML 2.0.
- Choose to Create. SAML app will be created.
- Now on the Create SAML Integration page, under General Settings, enter a name for your app.
- The logo field is optional
- Click Next.
- Under GENERAL settings, enter the Single Sign-On URL https://auth.lucideus.app/saml2/idpresponse.
- For Audience URI (SP Entity ID), enter urn:amazon:cognito:sp:ap-south-1_uanWqeAfG
- Under ATTRIBUTE STATEMENTS, add a statement with the following information:
- For Name, enter the SAML attribute name -http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress.
- For Value, enter user.email.
- Optionally- It is not mandatory to configure the following attributes since they do not affect SAFE integration with Okta. However, if they are configured, they will be synced with the respective fields for the onboarded users in SAFE, and SAFE Admin does not have to separately update these fields in SAFE whenever there’s an update in Okta.
- For First Name:
- For Name, enter the SAML attribute name -http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
- For Value, enter user.firstName.
- For Last Name:
- For Name, enter the SAML attribute name -http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
- For Value, enter user.lastName.
- For Mobile Phone:
- For Name, enter the SAML attribute name -http://schemas.xmlsoap.org/ws/2005/05/identity/claims/mobilephone
- For Value, enter user.primaryPhone or user.mobilePhone. (This has to be in international format without any symbol other than +, if this is added and the format is not as per the international format, the login will break for that user. Also, if in the profile of the user, one has set primaryphone but in an attribute value, one has set mobilePhone, it fails to fetch the number.)
- The overall attribute settings should be set as per the below screenshot:

- For First Name:
- Choose Next and Finish.
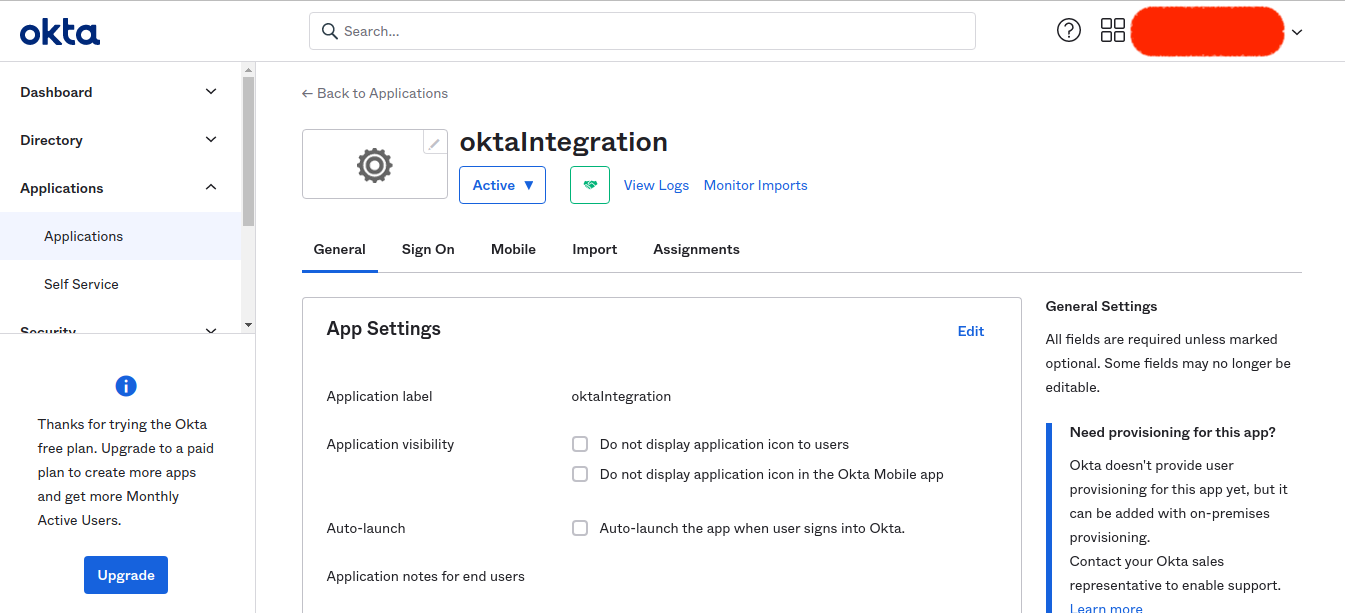
Assign a user to your Okta application
- First, onboard a user on the Okta developer console
- Navigate to Dashboard > Choose Directory > People > Onboard a user.
- Note: Onboard the user with the domain that should be there in the SAFE application. For example: USER@DOMAIN_GIVEN_TO_SAFE.
- Now assign that user to the Okta application you created.
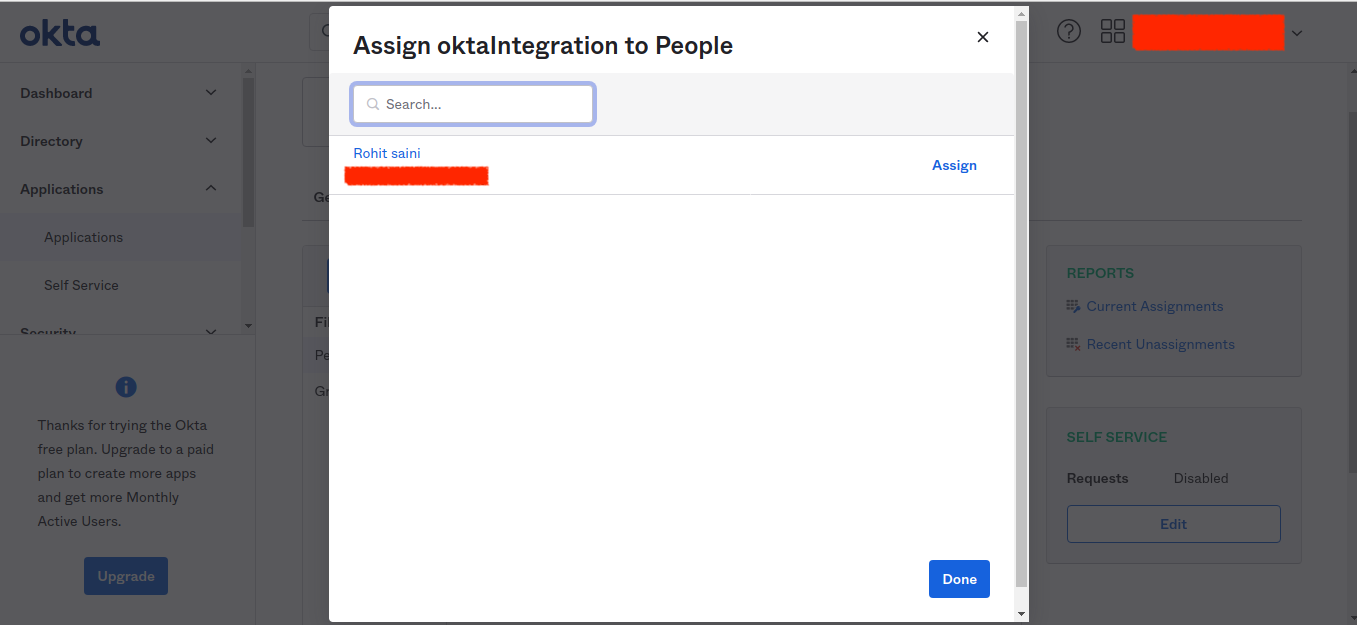
- On the Assignments tab for your Okta app, for Assign, choose Assign to People.
- Choose Assign next to the user that you want to assign.
- Note: If this is a new account, the only option available is to choose yourself (the admin) as the user.
- Choose Done and Go Back. Your user is assigned.
- Contact the SAFE Support team to do the required steps in AWS Cognito.
Adding User(s) to SAFE
- To log in to SAFE with an SSO-configured email, the customer must log in with the existing SAFE Admin user and add the users into SAFE. This can be done either by manually creating the user or by bulk uploading users from the User Management section in SAFE.
- Once the users are onboarded, they can start logging in to SAFE using their Email ID with the domain configured in SSO. On entering the correct Email ID, the Okta authentication page will open up, where they can enter their Okta credentials.
- After successful authentication, the login to SAFE will succeed.