About this document
This document provides step-by-step instructions to configure a Tenable Vulnerability Management (formerly known as Tenable.io) account in SAFE.
Introduction
The integration of SAFE with Tenable Vulnerability Management enables users to seamlessly discover and import assets along with their vulnerability and configuration assessment results. Users can choose to sync both vulnerability and configuration data at scheduled intervals or initiate an on-demand pull at any time.
Prerequisites
To configure the Tenable Vulnerability Management, you need the following details:
Tenable VM URL
Tenable VM Access and Secret Key (API Keys)
Tag filters - Apply filters to pull specific assets from Tenable VM.
Use multiple tag values separated by commas in this field.
Example: (Category1:Value1, Category2:Value2) to filter assets being synced.
Generate connection details
To connect Tenable VM with SAFE, you must create a new user with a Basic User role assigned with Can View permission for in scope assets plus Can Use permission for any filter tag that is to be used.
Create Permissions
To connect Tenable Vulnerability Management with SAFE, we must create a new user with following details
Role: Basic User
Permissions:
Can View for in scope assets
Can Use for any filter tag that is to be used
Create “Can View” Permission
Login to your Tenable Vulnerability Management account as Admin.
Click the Vulnerability Management card.
Click the Options menu available at the top-left of the screen.
Click Settings.
Click the Access Control card.
Click the Permissions tab.
Click the Create Permission button.
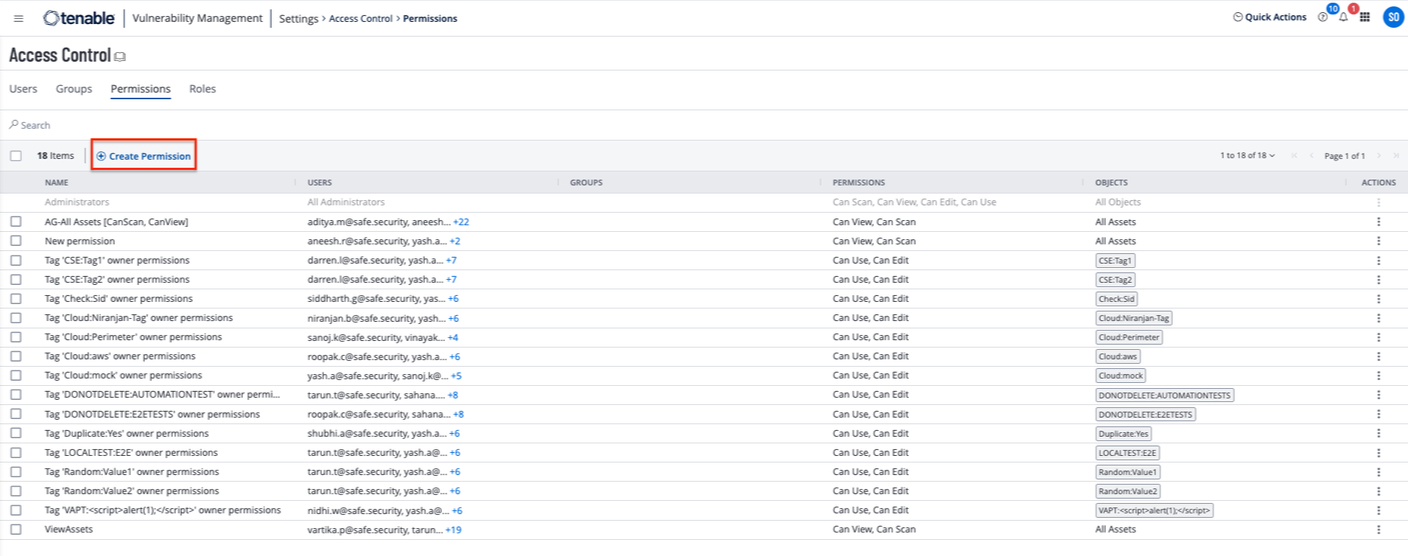
Enter the Permission Name.
Users and Groups field can be left blank here. We are creating permissions first and then will create a user with these permission.
Select Can View in the Permissions field.
Select All Assets in Object field.
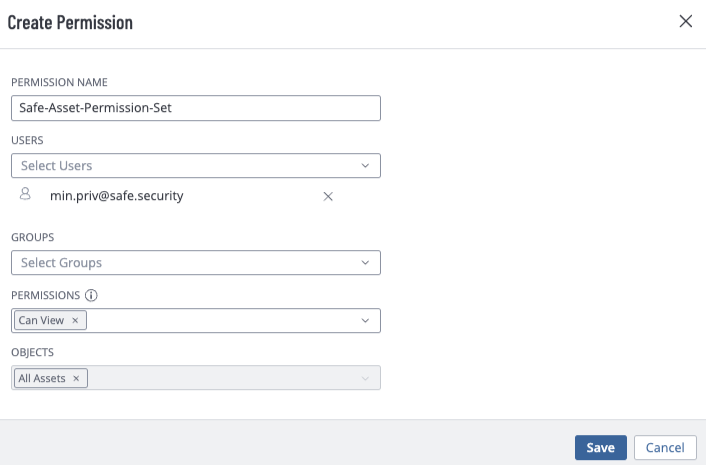
Click the Save button.
Create “Can Use” Permission
Follow the steps 1 to 7 of the Create Can View Permission section.
Enter the Permission Name.
Users and Groups field can be left blank here. We are creating permissions first and then will create a user with these permission.
Select Can Use in the Permissions field.
Select All Tags in Object field.
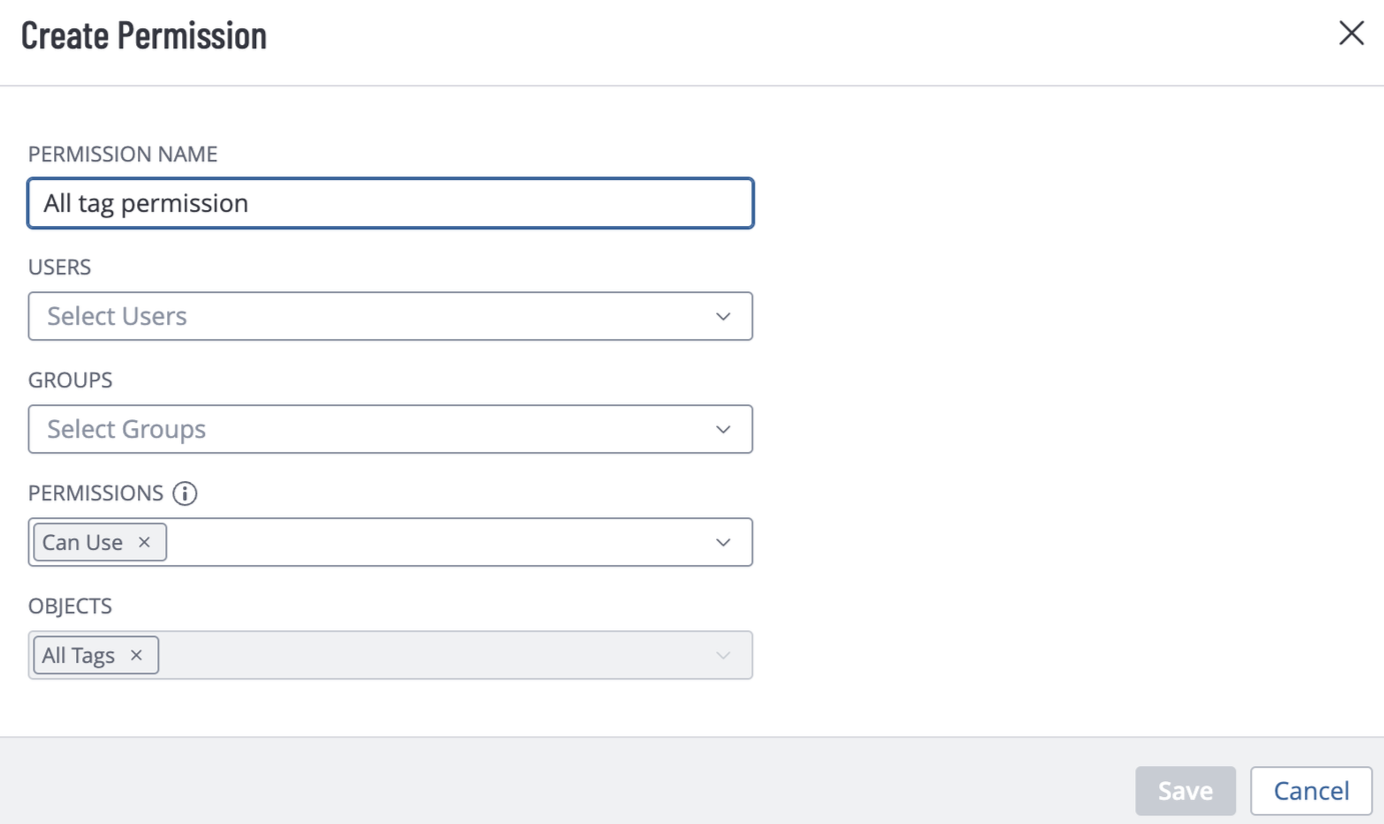
Click the Save button.
Create a User
To create a user:
Login to your Tenable Vulnerability Management account as Admin.
Click the Options Menu from top-left and navigate to Settings > Access Control Center.
On the Users tab, click the Create User button.
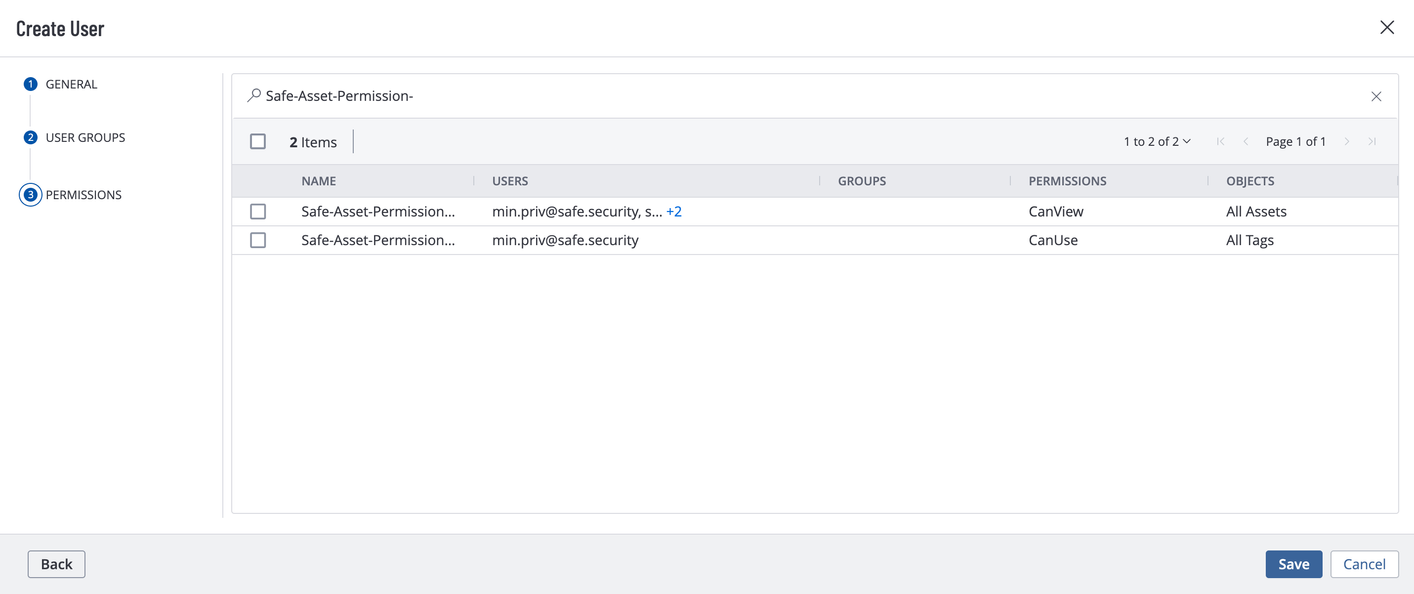
Enter the general details and users group details.
Add the Can View and Can Use permissions in the Permissions section.
Click the Save button.
Generate Access Key and Secret Key (API Key)
Login to your Tenable Vulnerability Management account with the newly created user’s credentials.
Click the Options Menu from top-left and navigate to Settings > My Account.
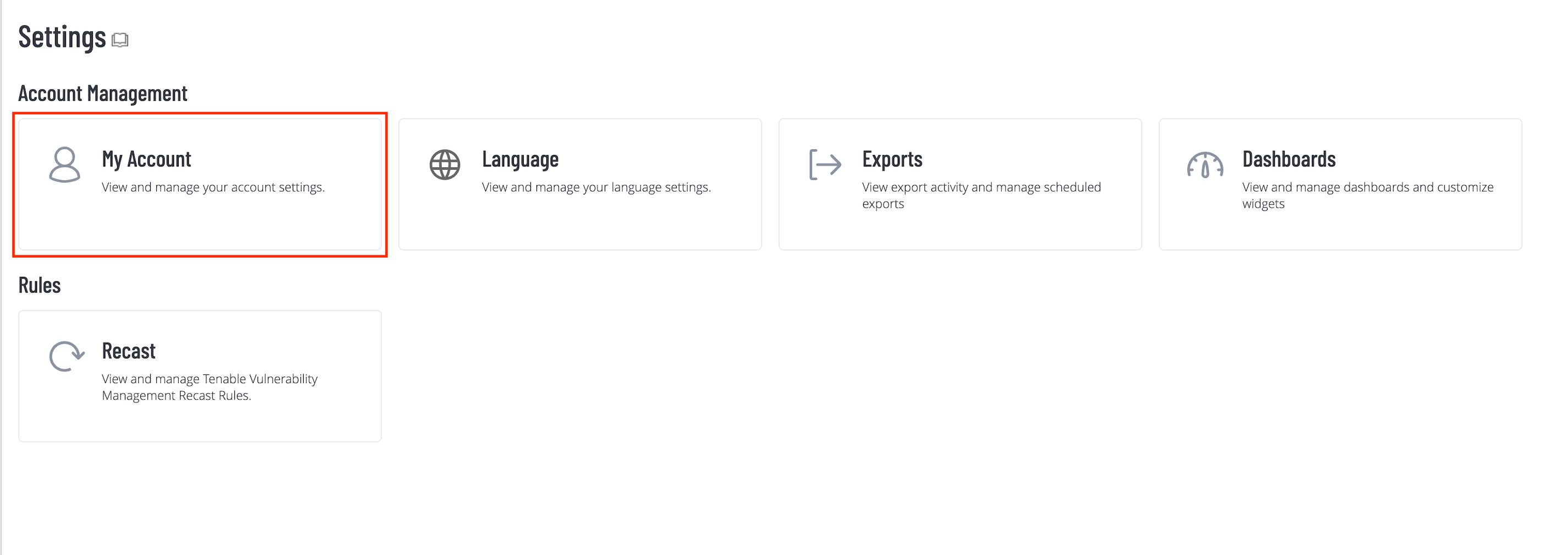
Click the API Keys tab.
Click the Generate button.
The system displays the API keys. Copy and save the API key to use it later while configuring Tenable Vulnerability Management in SAFE.
(Optional) Identify Tenable Vulnerability Management Asset Tags
This integration allows users to specify Tenable Vulnerability Management Asset Tags as filters for pulling selective assets and their related VA results.
The user must have access to use the Asset Tags. Refer to Edit a Permission Configuration to add the Can Use permission for the Tag and it’s value to the user. Alternatively you can add the CanUse permission for All Tags to the user.
To get Tags and their values, refer to Tags.
Configure Tenable Vulnerability Management
To configure Tenable Vulnerability Management in SAFE:
Navigate to Integrations.
Click the Plus button and search for Tenable Vulnerability Management.
Click the Tenable Vulnerability Management card.
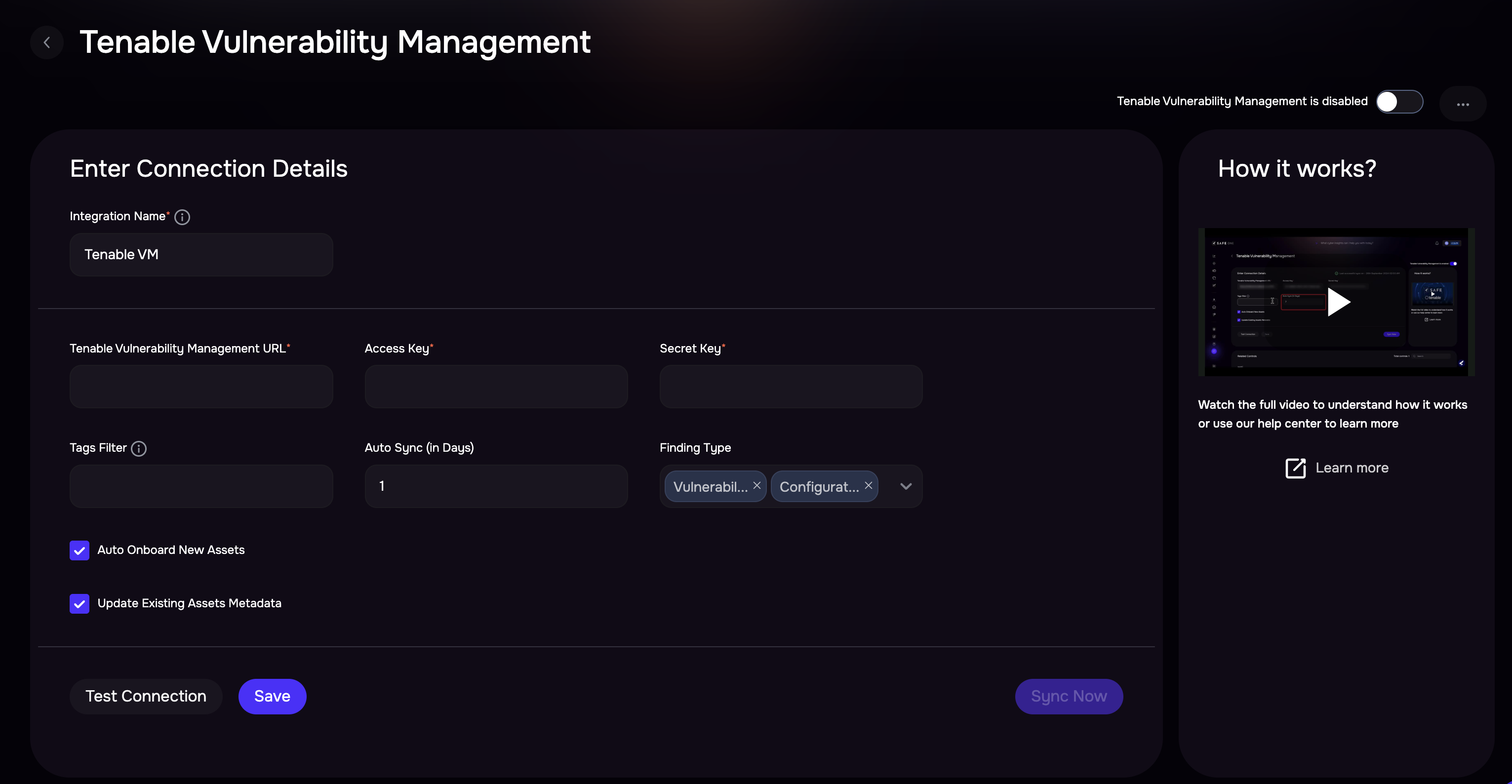
Enter the Name, Tenable URL, Access Key, Secret Key, and Auto-Sync frequency. Refre to /safe-4/docs/tenableio#generate-connection-details
(Optional) Enter the Tags Filters.
Use multiple tag values separated by commas in this field.Example: (Category1:Value1, Category2:Value2) to filter assets being synced.
Select the Data Type as Vulnerability Assessment, Configuration Assessment, or both.
At least one data type (Vulnerability Assessment or Configuration Assessment) must be selected. The field cannot be left empty.If needed, uncheck the Onboard Asset checkbox.
Onboard Assets - By default, any assets in Tenable Vulnerability Management that are not found in SAFE will be onboarded. To limit the integration to pull in vulnerabilities of only the assets that are present in SAFE, this option can be unchecked.If needed, uncheck the "Update Existing Assets Metadata" checkbox.
Update Existing Assets Metadata: If this checkbox is marked, the asset's metadata, such as asset name, IP address, etc., will get updated based on the data pulled from Tenable Vulnerability Management.
Click the Test Connection button.
Once the connection is verified, click the Save button.
Once the configuration is saved, click the Sync Now button to trigger the on-demand sync outside of the Scheduled Auto Sync. The Auto Sync time is 04:30 UTC.
Notes
When using Tenable VM CA findings, please be aware of the following:
Findings overwrite during full syncs
If Tenable VM runs a full sync, all CA findings for matched assets will be replaced with Tenable VM CA findings.
This means CA findings from other tools (e.g., Tanium, Azure) will be removed if they overlap on the same assets.
Full sync happens only in certain cases:
If a previous sync failed or was partial.
If the integration is reconfigured.
Regular syncs are incremental and do not overwrite findings from other tools.
There is no automatic weekly full sync.
Importing Tags from Tenable Vulnerability Management into SAFE
Ensure that Tenable Vulnerability Management integration is configured.
Create Custom Fields in SAFE that correspond to the tag keys (category) in Tenable Vulnerability Management that you wish to import. To set up these custom fields, go to Settings > Custom Fields.
During the next sync with Tenable Vulnerability Management, the system will automatically update the custom field values. If you prefer, you can manually trigger a sync by going to SAFE Hooks > Tenable Vulnerability Management.
Info
The system will only import tags from Tenable Vulnerability Management if the corresponding custom fields are already set up in SAFE.
After each subsequent scan, the custom field values will be automatically updated.
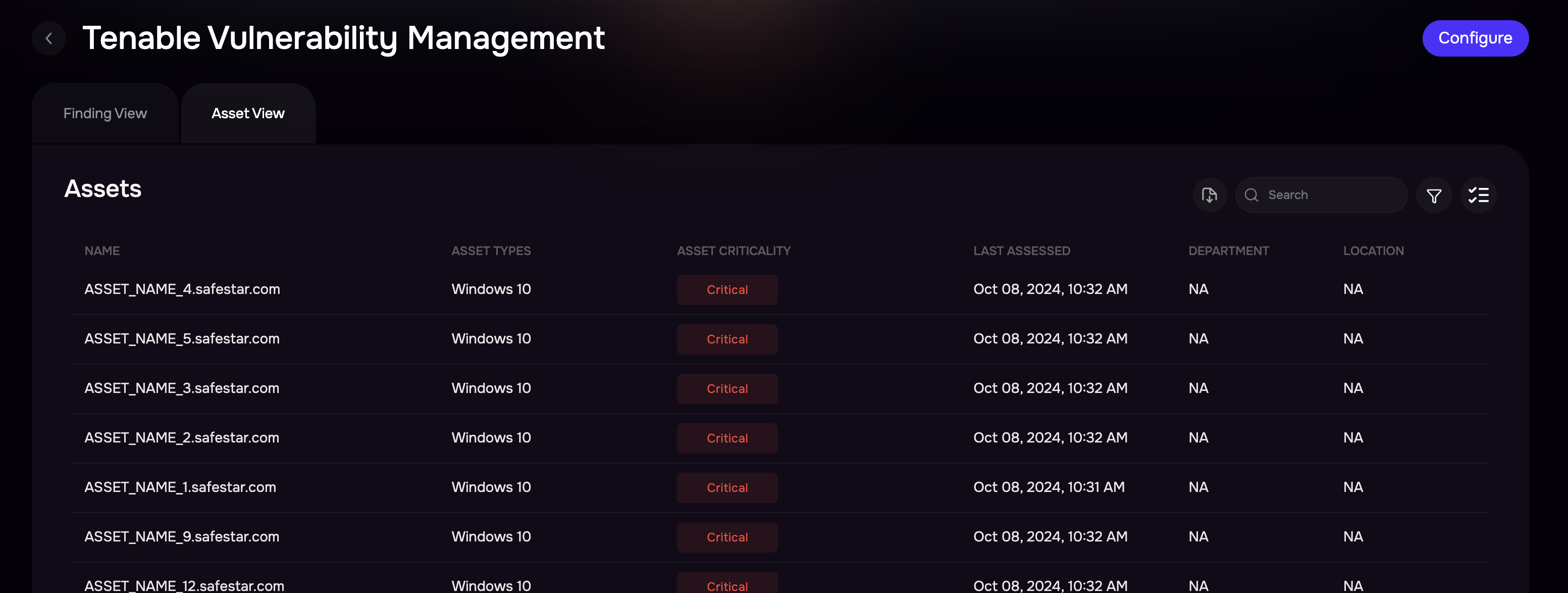
View Result
Once Tenable VM is configured, SAFE pulls all the VA and CA scan results from Tenable.
To view the assets and findings pulled from Tenable VM
Go to the Integrations.
Search and click the Tenable VM card.
The page displays Assets and Findings in two different tabs.
History
Learn More about Integration History here.
FAQs
1. Why does SAFE use both Full and Incremental sync modes when fetching assessment/analysis data from Tenable Vulnerability Management, and when does it switch between them?
SAFE employs two sync modes, Full and Incremental, when fetching assessment/analysis data from Tenable Vulnerability Management. The Full sync mode retrieves data for the last 90 days, and it is initiated at the First-time Sync. When SAFE is executing sync for the first time, it runs in Full mode to fetch a comprehensive set of data.
Once a successful Full sync has been completed, SAFE transitions to Incremental sync mode for all subsequent sync operations. Incremental sync fetches only the data that has been updated or added since the last successful sync, optimizing the synchronization process for efficiency and speed. This switch to Incremental sync mode ensures that SAFE stays up-to-date with the latest changes from Tenable while minimizing the amount of data transferred during synchronization.
2. Can SAFE be configured to prioritize recasted severity from Tenable Vulnerability Management instead of the default CVSS score when pulling in assessment data?
By default, SAFE prioritizes severity based on the CVSS score. However, if users wish to explicitly prioritize the recasted severity from Tenable Vulnerability Management, it is possible to configure this behavior using the PATCH /integration API.
To enable SAFE to pull in recasted severity, users can set the "scoringPriority" flag in the Tenable Vulnerability Management configuration using the PATCH /integration API. Set the value of the "scoringPriority" flag to "severity." This configuration change will instruct SAFE to prioritize the recasted severity from Tenable Vulnerability Management, allowing users to customize the assessment data based on their specific requirements.
3. I’m not sure what the assetMatchingCriteria should be for my Tenable Vulnerability Management instance.
The assetMatchingCriteria is something that SAFE uses to map Tenable Vulnerability Management Assets' VA data to SAFE assets. What is important is that a field is picked that can uniquely key together existing assets in SAFE and assets in Tenable. It can be simplified in 2 ways:
If the Tenable Vulnerability Management Asset(s) for which the VA data is being pulled can be identified uniquely using the FQDN or Hostname value in Tenable Vulnerability Management, we can use the default assetMatchingCriteria. In this situation, no customization will be needed. In case any asset does not have a value for FQDN or Hostname fields in Tenable Vulnerability Management , in that scenario, IP Address will be used to identify the Asset.
If the Tenable Vulnerability Management Asset(s) for which the VA data is being pulled can be identified uniquely by IP Address value in Tenable Vulnerability Management , we need to give higher precedence to IP Address in asset matching criteria. The assetMatchingCriteria in such a situation would become ["ipAddress","fqdn", "assetName", "macAddress"]. If an IP address is not available, then FQDN/Hostname will be used to identify the asset.
Info
To check the assetMatchingCriteria, use the below API
GET <SAFE_URL>/api/v3/settings/os-to-safe-asset-type-mapping
To add a custom assetMatchingCriteria based on your requirements, use the below API
POST <SAFE_URL>/api/v3/settings
4. Is it mandatory to provide tags in Tenable Vulnerability Management Configuration?
No, providing the tags in the Tenable Vulnerability Management configuration is not mandatory. Tags help a user configure a filter for the assets whose VA data is pulled by SAFE. This is useful in case Tenable Vulnerability Management has a large data set, and the user only wants to import a section of the data in SAFE.
5. Is it possible to update an already stored Tenable Vulnerability Management configuration?
Yes, it's possible to update a stored configuration. Users can go to UI and follow the configuration steps again.
6. I’m not able to trigger a sync action over a Tenable Vulnerability Management.
Make sure the stored credentials are still valid.
The Sync Now option is not available while there is an ongoing In Progress sync. If a sync is running for 24 hours there is a timeout to re-enable the Sync Now option.
7. Which CVSS score does Tenable Vulnerability Management integration use?
We use the CVSS V3 score if it is present. If the CVSS V3 is absent, then the CVSS V2 score is considered.
8. If I mark Accepted Failed from SAFE, what would happen in the case of Tenable Vulnerability Management ?
Tenable Vulnerability Management will only comply with the Accepted Risk marked in Tenable Vulnerability Management . In case you mark a control as Accepted Failed in SAFE, it will get overridden in the next sync of Tenable Vulnerability Management .
9. There are some duplicate assets in Tenable - how does SAFE handle them?
SAFE uses the asset matching criteria to determine which asset to post the data to. If there are duplicate assets in the source, the order of data received in API determines which asset’s vulnerability remains synced in SAFE. The recommendation is to clean the data at the source.