About this Document
This document provides a detailed guide to integrating AWS Security Hub with SAFE.
AWS Security Hub is a native AWS service that centralizes and standardizes security findings across AWS services and resources. By integrating AWS Security Hub with SAFE, organizations can:
Onboard individual or master AWS accounts into SAFE.
Automatically ingest AWS assets and security misconfigurations.
Prerequisites
Before configuring the integration, ensure the following prerequisites are met:
AWS Security Hub Enabled
Security Hub must be enabled in the AWS account(s) you want to onboard.
If using a master account, member accounts must be invited and Security Hub must be enabled in the required regions.
AWS Permissions
SAFE uses an IAM Role with read-only access to discover resources and fetch findings.
The following AWS-managed policies must be available:
AmazonEC2ReadOnlyAccess
AWSSecurityHubReadOnlyAccess
These policies are automatically attached to the IAM Role created via the CloudFormation stack provided by SAFE.
CloudFormation Stack Deployment
SAFE provides a CloudFormation template (SafeSecurityAwsSecurityHubOnboardingStack.template.json) to automate IAM role creation.
Users must have sufficient permissions in AWS to deploy the stack.
User must be logged in as a SAFE Admin role to add AWS integrations.
Configure AWS Security Hub in SAFE
SAFE allows users to add both master and member AWS accounts. You can onboard an Individual AWS Account in SAFE via the Role method.
SAFE admin can onboard AWS accounts by following the below step-by-step instructions:
Navigate to Integrations from the left navigation.
Click the “+” add integration button and search for AWS Security Hub.
Click the AWS Security Hub card.
.png)
(Optional) If required, set the expiry date for the link as follows:
Mark the checkbox to Set the expiry date and time for the generated link.
Enter or select the expiry date and time from the calendar.
Click the Generate button.
.png)
The system generates a CloudFormation stack link. You can copy and paste the link into a new tab in the browser. The link redirects you to the AWS console page.
If asked by the system, log in to your AWS account that you want to onboard - by default it will try to onboard the already logged in AWS account.
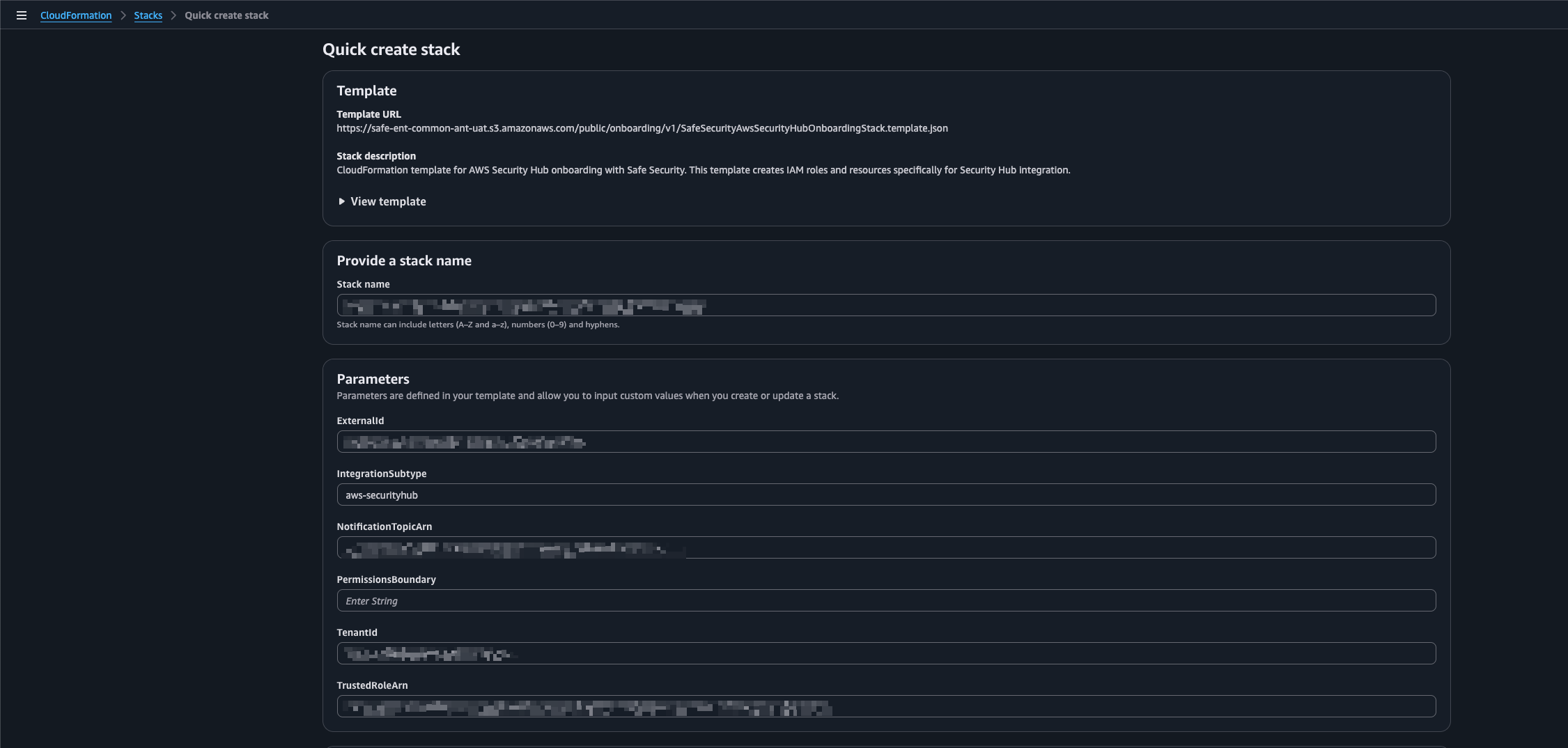
The system displays a pre-filled Quick create stack page.
(Optional) If necessary, add the Permission Boundary ARN. SAFE supports adding the Permission Boundary ARN via an input text box in the quick create stack page to allow attaching the permission boundary to the IAM role (that is created as part of the stack).
Mark the checkbox to acknowledge that AWS CloudFormation might create IAM resources with custom names.
Note: The CloudFormation template creates an IAM role and assigns read-only privileges to it. This access privilege is then used by SAFE during the automated/on-demand assessment of all supported services available under that cloud account.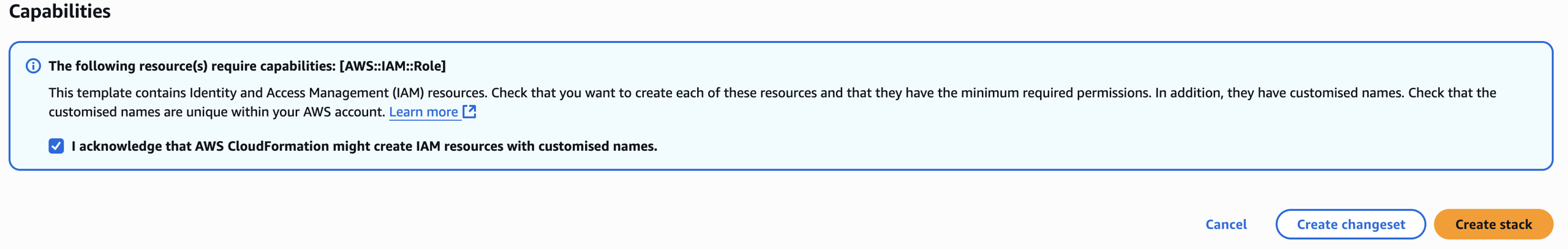
Click the Create stack button. The system might take a few minutes to create the stack, usually between 3 to 5 minutes.
Note: If the user has previous onboarded the same account on same tenant, the user will require to delete the existing stack before creating the new stack to onboard the AWS account again.
SAFE auto-discovers your AWS account and displays it under Configured Accounts.
Manage AWS Accounts
View Configured AWS Account
To view the onboarded AWS account:
Navigate to Integrations.
Click the AWS Security Hub card.
The system displays a list of all the configured accounts on the page.
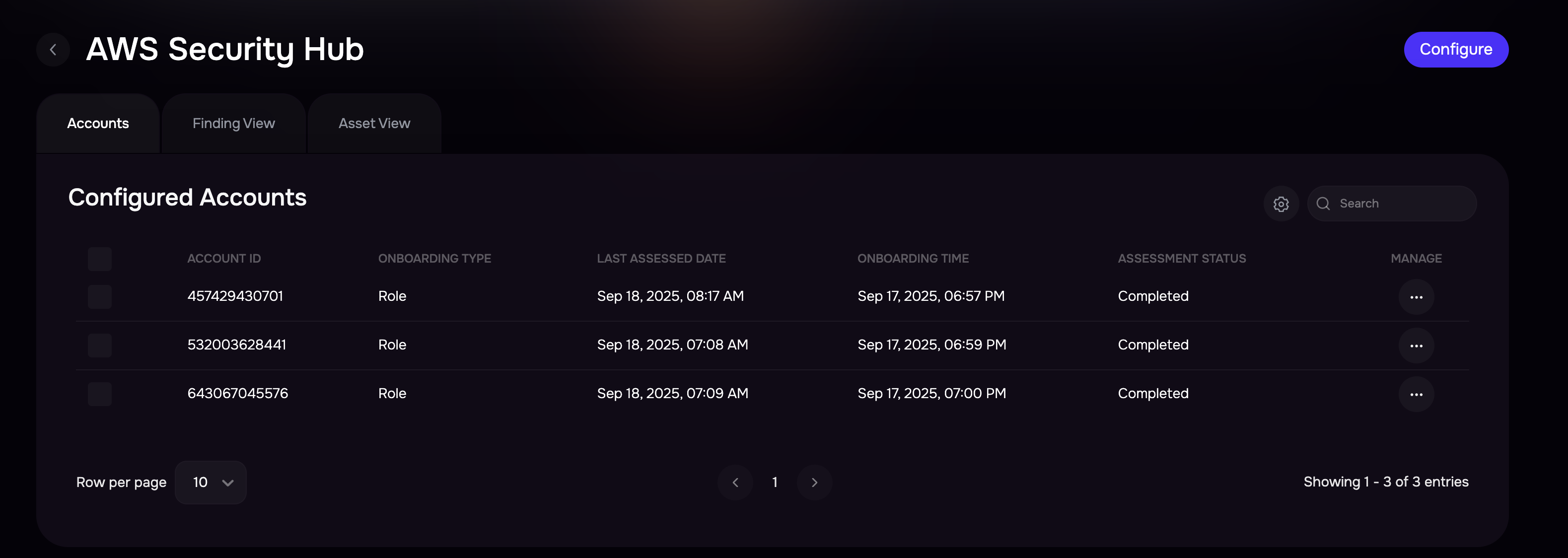
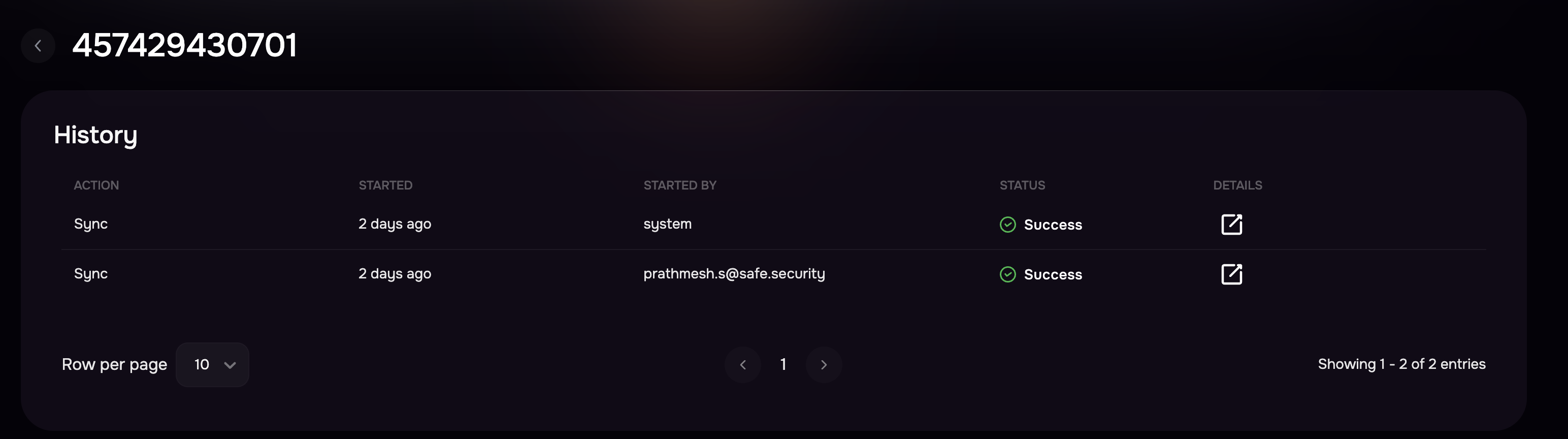
View sync history for AWS Account(s)
Multiple accounts from AWS can be onboarded and assessed into SAFE. To view the sync history of individual accounts, click on the Account ID in the “Configured Account” section. The page will show the sync history for the account.
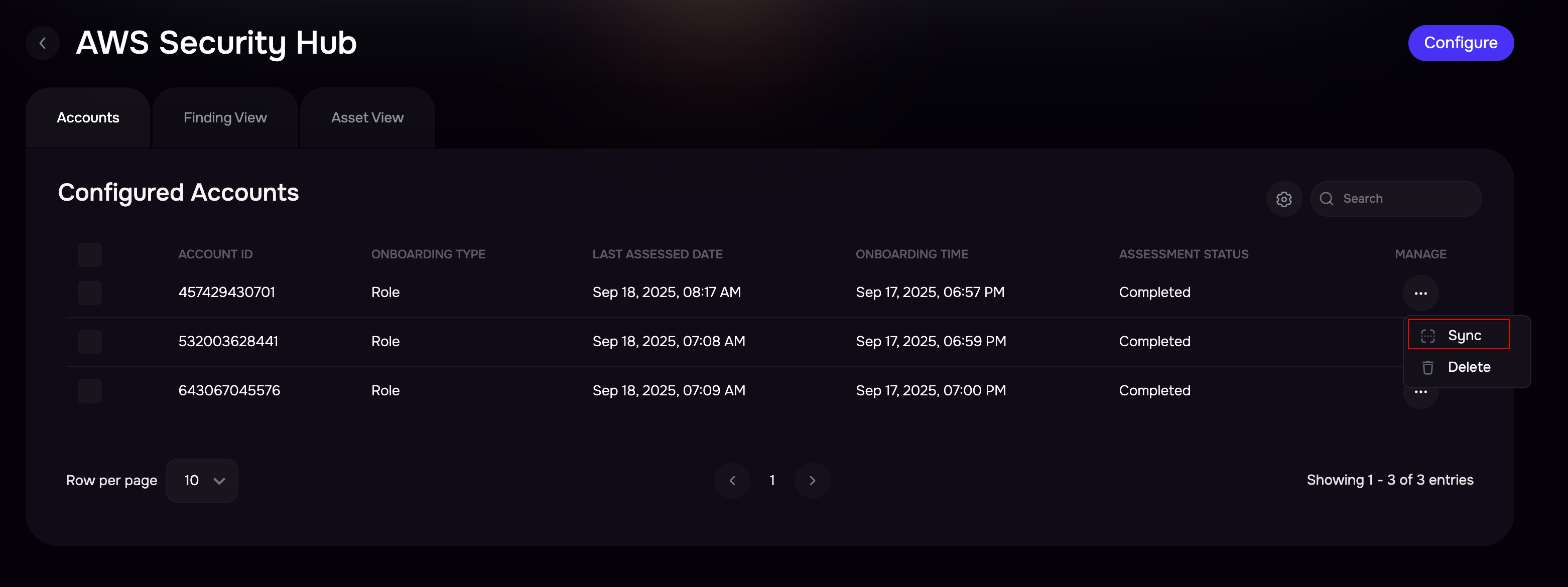
Manually Sync AWS Account
To start a manual sync:
Click the options menu available in the Manage column.
Click the sync button. The system notifies you that a sync has been started. The status of the sync will be displayed under the “Assessment Status” column.
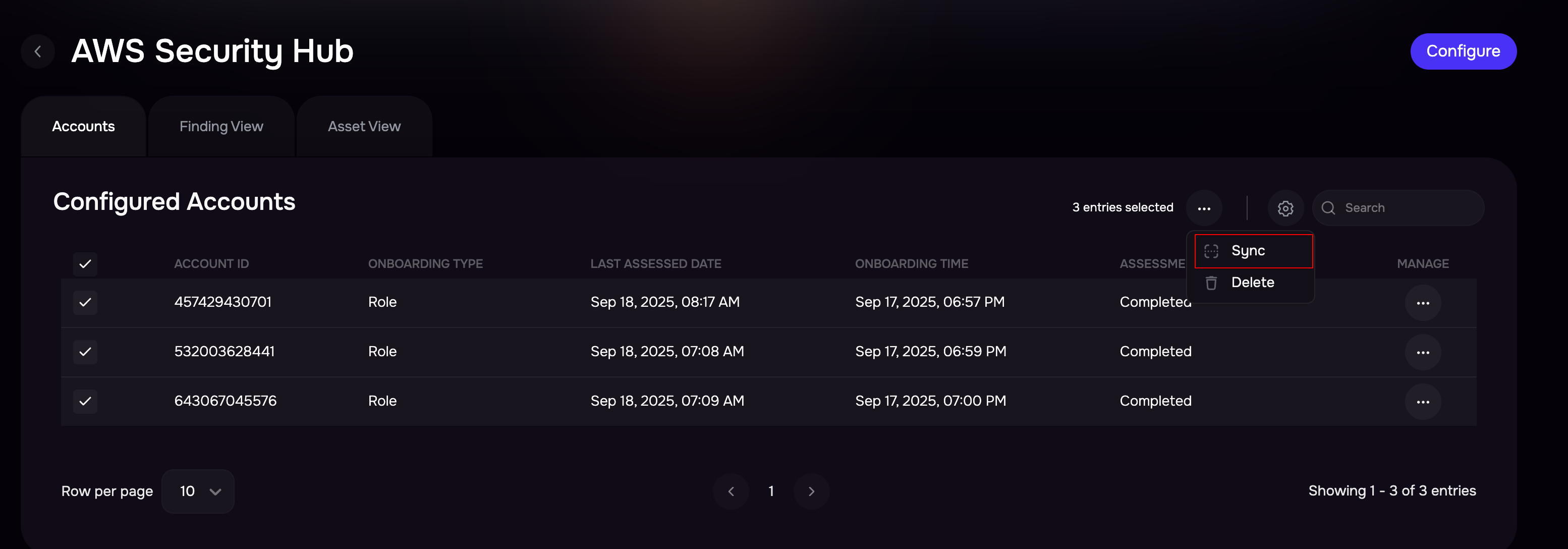
Manually Sync AWS Account in bulk
Users can start the sync of multiple AWS accounts from the AWS configuration page.
To start the sync in bulk:
In the section for Configured Accounts, select the AWS accounts by marking the checkboxes available against them.
Click the Sync icon available at the top to start the sync.
Delete AWS Account(s)
To delete multiple AWS account(s):
Navigate to the integration configuration page.
In the section for Configured Accounts, select the AWS accounts by marking the checkboxes available against them.
Click the Delete option from top menu
click the “Yes, Delete” button on the confirmation screen.
AWS account can also be deleted individually by choosing the delete option from the “Manage” column menu.
Note : The CloudFormation stack created for the onboarded account must be deleted manually in the AWS account itself to support onboarding the same account in the future.
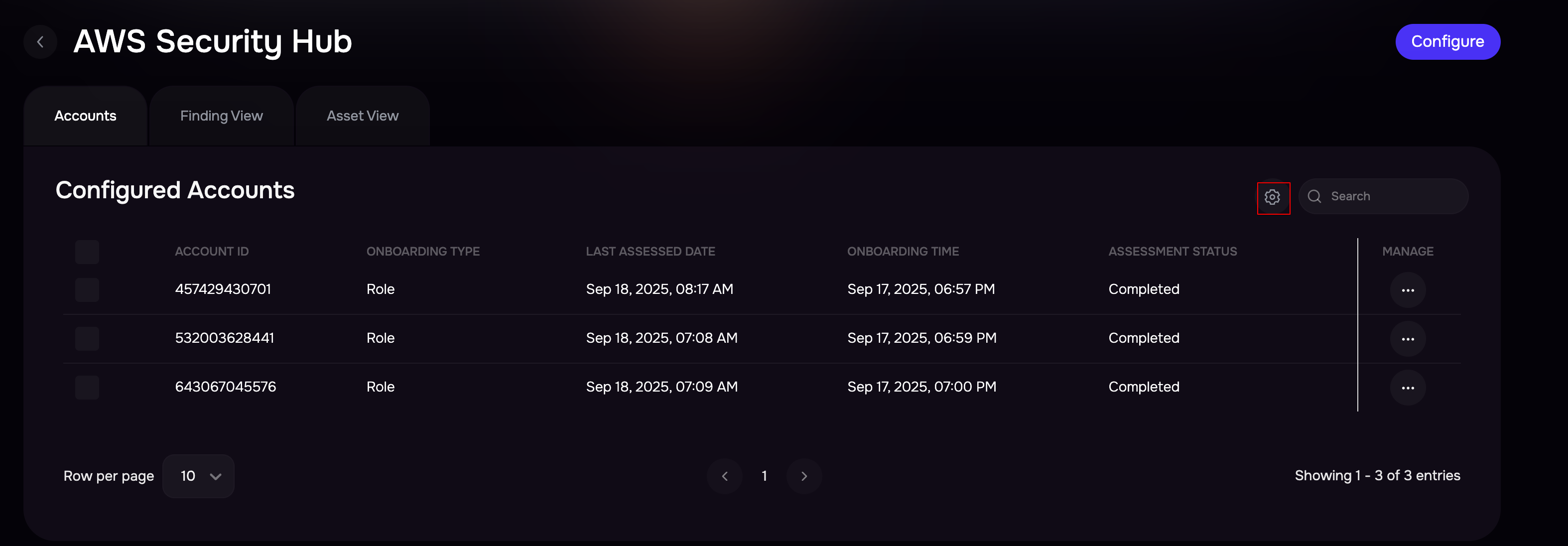
Set Global Sync Frequency for onboarded AWS accounts
Users can set Global Sync Frequency (frequency for syncing the onboarded AWS account as a number of days).
To set the auto-sync frequency for onboarded AWS accounts:
In the section for Configured Accounts, click on the setting icon at the top.
Enter the number of days in the Global Sync Frequency field.
Click the Update button.
View results
SAFE syncs the added AWS accounts and automatically onboard the assets in SAFE.
Click the AWS Security Hub card.
Click the Asset View” tab to see all the AWS assets .
.png)
To view Findings assessed:
Go to Integrations from the left navigation.
Click the AWS Security Hub card.
Click the “Finding View” tab to see all the findings.
FAQs
I can’t see all Security Findings in SAFE. Why?
Currently, SAFE supports configuration findings only from AWS Security Hub.
The following finding types are ingested into SAFE:
Software and Configuration Checks / Industry and Regulatory Standards
Effects* – All finding types starting with “Effects”
Software and Configuration Checks / AWS Security Best Practices / External Access Granted
Software and Configuration Checks
If I pause or stop an EC2 instance, will SAFE still assess it?
Yes. SAFE continues to assess onboarded assets regardless of their runtime state, as long as the AWS account is regularly synced.
If I set an expiry date for a stack-creation link (e.g., 7th Apr 2021), when will it become inactive?
The link becomes inactive from 12:00 AM on 8th Apr 2021.
What happens if I use the stack-creation link after it has expired?
The stack can still be created using the link, but the associated AWS account will not appear in SAFE.
What if I create another stack in an account that already has one?
You can deploy multiple stacks in the same AWS account only if they are linked to different SAFE instances.
If you attempt to create another stack for the same SAFE instance, the stack creation will fail.
Resolution:
Delete the previous stack before deploying the new one.
Once deleted, the account will no longer be assessed in SAFE until the new stack is deployed.
If the next scheduled sync occurs before deploying the new stack, the assessment status will show as Failed.
What happens if I delete an AWS account from SAFE while a sync is in progress?
The ongoing sync will continue in the background, but the results will not be updated in SAFE.
Why is the Add Account button disabled even though I’m logged in as an Admin?
Please contact the SAFE Support Team to enable the Add Account option.
Which IAM role, permissions, and connectivity method does SAFE use?
SAFE uses a CloudFormation stack to create an IAM role with read-only access.
The following AWS-managed policies are applied:
AmazonEC2ReadOnlyAccess
AWSSecurityHubReadOnlyAccess
The CloudFormation template used is:
SafeSecurityAwsSecurityHubOnboardingStack.template.json
SAFE assumes the IAM role created through this template to generate temporary credentials for accessing AWS Security Hub findings and resources.
Can I use a custom AWS role instead of SAFE’s CloudFormation stack?
No. SAFE only supports the IAM role provisioned via its provided CloudFormation template.
Is AWS Security Hub account-level or region-level?
AWS Security Hub is an account-level service, but it must be enabled region by region.
What is Cross-Region Aggregation in AWS Security Hub?
Cross-Region Aggregation allows findings from multiple regions to be aggregated into a single home region.
The home region is designated when enabling Cross-Region Aggregation.
Security Hub must be enabled in all required regions for aggregation to work.
Do I need Cross-Region Aggregation enabled for SAFE to fetch findings?
No. SAFE’s connector automatically iterates through all regions where Security Hub is enabled.
Findings can be fetched with or without Cross-Region Aggregation.
How do I enable multi-account findings collection in Security Hub from a master account?
To enable multi-account collection:
Invite member accounts into AWS Security Hub from the master (administrator) account via the Security Hub CSPM console.
Enable Security Hub in the master account across the required regions.
This ensures findings from both master and member accounts are available in SAFE.
If I onboard a master account into SAFE, which findings and resources are ingested?
Master Account: Findings and resources from all regions where Security Hub is enabled.
Member Accounts: Findings and resources from all regions where Security Hub is enabled, provided the member accounts have been invited and enabled in Security Hub CSPM.