About this document
This document provides step-by-step instructions to configure "Prisma Cloud" in SAFE and pull findings from AWS, Azure, and GCP configured on Prisma.
Note
This integration only supports the standard policies or templates in the source product for use in Risk Scenario calculations in SAFE based on their mapping to FAIR CAM controls
Introduction
This integration allows you to onboard your cloud assets from Prisma Cloud and fetch configurational assessment findings from Prisma into SAFE. SAFE Admins can configure this integration from the "Prisma Cloud" card available on the Integrations page.
Configuring this integration will provide insights into the configurational security posture of the cloud environment which will be correlated with metrics from other parts of the organization and provide CRQ with Actionable steps.
Prerequisites
Cloud Accounts onboarded into Prisma
A Prisma user with a System Admin role OR with enough permissions to create a Service Account with an “Account Group Read Only” role
SAFE access with an admin role
Generate connection details
To integrate SAFE with Prisma, we need 2 details to be generated from the Primsa Cloud portal:
Access Key ID
Access Key Secret
Prisma ID (optional)
To generate these details, a user-type service account will be created in Prisma, which will provide us with the above-required details.
Create a read-only permission role in Prisma
Log in to your Prisma Portal
Open Settings
.png)
If not already present then we need to create an “Account Group Read Only” role.
From the left navigation menu open Access Control → Click on Add dropdown and choose Role
.png)
Add a Name for the role and description (optional). Then from the “Permission Group” dropdown → select “Account Group Read Only”.
.png)
In the Account Group dropdown → select the “Default Account Group" option and click on Submit.
.png)
A new role will be created and shown under the Role tab.
.png)
Create a service account user in Prisma
Under Access Control → Click on Users Tab → Click on the Add dropdown button and choose Service Account
.png)
Give any name of the Service Account User and choose the role created in step 3. Then click Next.
.png)
Give an identifiable name to the Access Key. Click on Save & Create
.png)
Prisma Gives the option to enable the expiration of these access keys, which can be enabled as per user/customer needs. Once the Access Key creds expire the user would need to generate updated credentials from Prisma and update them into the SAFE portal.
Access Key ID and Secret Access Key will be displayed. Copy them to a secure place as they will be needed to configure the Prisma integration in the SAFE portal later.
.png)
Configure Prisma Cloud in SAFE
During Prisma configuration, users have the option to add an optional parameter called "Prisma ID". While Prisma integration typically works with just the Access Key ID and Access Key Secret, this additional parameter is considered optional by Prisma themselves. However, in rare instances where the "Test connection" fails despite using the correct credentials, users can attempt adding the Prisma ID as a troubleshooting step to see if it resolves the issue.Follow the below steps to configure Prisma Cloud in SAFE.
Go to the Integrations page and click the "Prisma Cloud" card.

Open the Configure page.
Enter the Prisma Cloud API URL. This can be found on this page and is based on the Prisma Cloud’s portal URL (Click Here)
Enter the Access Key ID and Access Key Secret Generated above.
Excluded Cloud Type (optional):
By default, SAFE will pull findings from Prisma for all the assets across 3 clouds (AWS, Azure, and GCP).
This dropdown is optional but gives the user flexibility to sync only selected Cloud platforms.
For example: Selecting “Azure" from the dropdown will exclude it from Sync and assets from AWS and GCP will be synced from Prisma.
Cloud Account Ids (Optional):
By default, SAFE will pull all the assets and their findings from Prisma across all the cloud accounts.
This field is optional but gives the flexibility to sync only to provide cloud account IDs from the cloud platform(s).
Multiple Account ID(s) of any cloud platform can be provided in this field separated by commas.
For example: “aws-account-id-1”, “aws-account-id-2”, “gcp-account-Id-1”, “azure-account-id-1”, “aws-account-Id-3”
Exclude Prisma Asset Types (Optional):
By default, SAFE will pull all the assets from Prisma based on the access level of the provided credentials.
This field is optional but gives users the flexibility to filter assets to be not pulled into SAFE based on the asset type present in Prisma.
The provided asset type values should match exactly in Prisma for exclusion to work.
For this, in your Prisma portal, navigate to the list of assets in the Inventory section, and the values in the “Asset Type” column can be added in SAFE.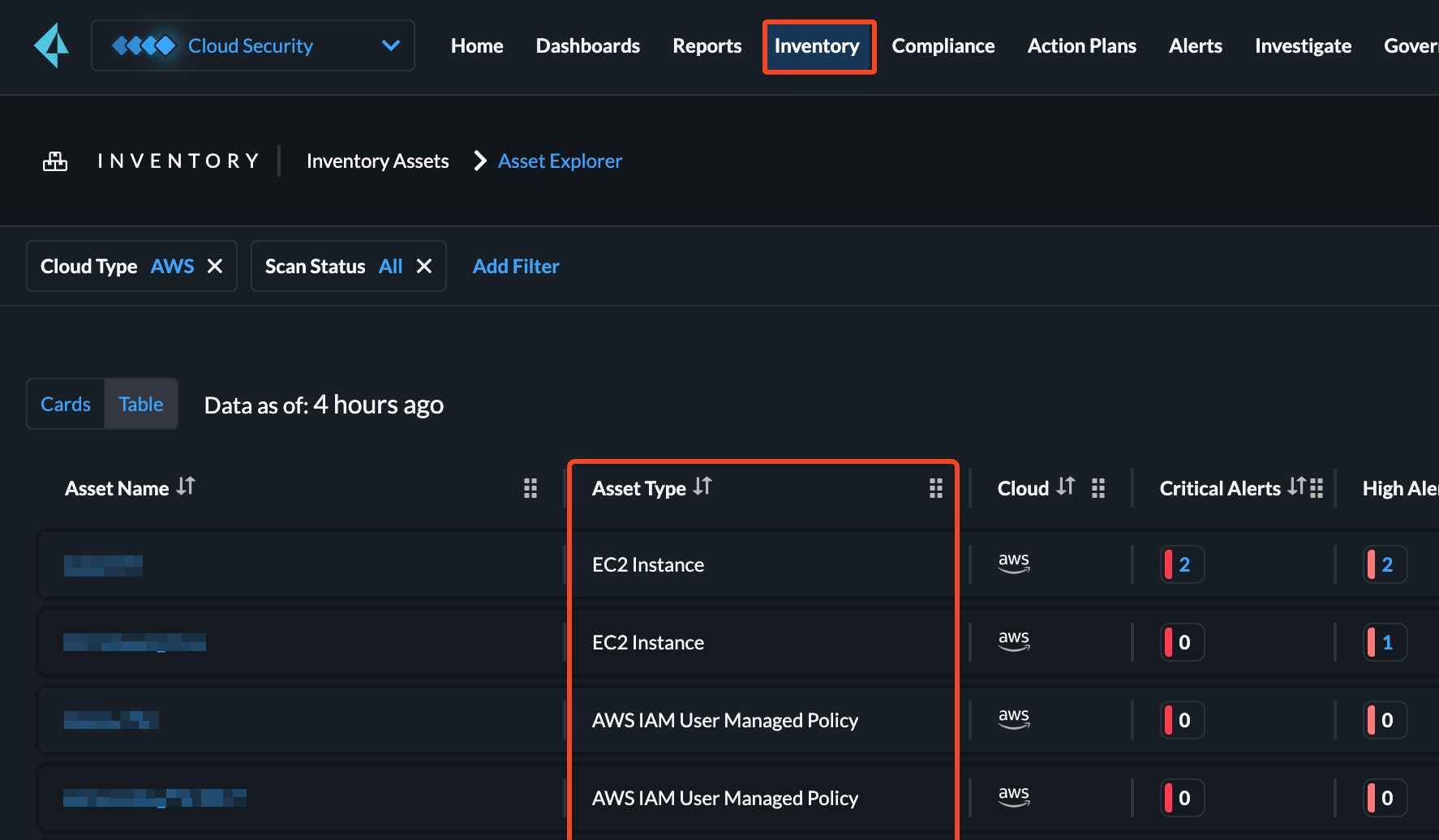
If needed, uncheck the"Update Existing Assets Metadata" checkbox.
Update Existing Assets Metadata: If this checkbox is marked, the asset's metadata, such as asset name, etc., will get updated based on the data pulled from Prisma.
If needed, mark the Auto Onboard New Assets checkbox.
Onboard Assets - By default, any assets in Prisma Cloud that are not found in SAFE will be onboarded. This option can be unchecked to limit the integration to pull in findings of only the assets present in SAFE.Click the Test Connection button.
Once the connection is validated, click the Save button.
Once the configuration is saved, click the Sync Now button to trigger the on-demand sync outside the scheduled auto sync.
View Result
To view the assets and the assessment result:
From the Integrations page, Click on Prisma Cloud card.
A page with “Finding View” and “Asset View” tabs will open up.

The finding view will contain all the findings pulled from Prisma.
Asset view will have a list of all the assets pulled/updated from Prisma.
Alternatively, you can navigate to Technology and filter the asset list to find source equals Prisma Cloud.

FAQs
What cloud platform does SAFE support and pulls from Prisma?
SAFE pulls data from 3 clouds: AWS, Azure, and GCP
I want to sync only selected account Ids from Prisma Integration. How can I do that?
The "Cloud Account IDs" field allows users to select specific accounts from which they want data to be pulled from Prisma. These accounts are treated with higher priority during synchronization.
Example:
A user provides account IDs for AWS and GCP but not Azure.
Even though Azure is not explicitly excluded from the synchronization, SAFE will prioritize the provided IDs.
Consequently, SAFE will only pull data from AWS and GCP, ignoring Azure data.
To include data from Azure, users need to explicitly include Azure account IDs in the "Cloud Account IDs" field.
Why am I seeing a difference in the total asset count shown by Prisma Cloud vs What is processed and pulled SAFE?
SAFE imports cloud assets that have been scanned by Prisma Policies. These policies must have severity levels of Low, Medium, High, or Critical. Informational policies are not included in SAFE.
Example 1: Asset with Informational Policies
An asset scanned by Prisma for five policies, all with informational severity, won't be imported into SAFE. Consequently, no findings will also be pulled.
Example 2: Asset with Mixed Severity Policies
Another asset scanned by Prisma for five policies has two informational and three high-severity policies. This asset will be imported into SAFE, but only the three high-severity findings will be included.
What happens if I exclude Azure from the Sync but still provide an account ID from Azure in the “Cloud Account ID” box?
Only data from those account IDs will be pulled which are not excluded from the sync. In this case, even though the account ID is provided as it's excluded from the cloud type, the data from Azure will not be pulled.